
But there are also many illegal activities that happen on the dark web. And just like in real life, using the dark web for criminal purposes is never legal. The Tor network combined with a VPN is one of the safest ways to get on the dark web.
Other Built-in Tor Features You Should Know
There are reports of illegal services on the dark web, ranging from paid assassinations to the trafficking of sex and weapons. However, some of these alleged services, such as professional ‘hitmen,’ may be scams designed to defraud willing customers. Privacy and anonymity are the core values of the dark web, and it hosts both harmless activities and illegal content.
Is It Illegal To Browse The Dark Web?
Even without the code, you can visit the security section to get tips on improving your daily life privacy. This service is a good source of statistics if you have a school project requiring research on Tor and the dark web. However, note that the site only uses non-sensitive and public data for the metrics.
No Protection Against Malware
One of its key benefits is unlimited bandwidth, which sounds awesome and allows for unlimited dark web browsing. It encrypts your traffic right away, which is beneficial if you don’t want your ISP to see you’re using Tor. Some countries frown upon dark web usage, so it’s good to have your back covered by a reputable VPN service. Select your platform, click on it, and Tor will download in seconds.
Essential Tools For Secure Dark Web Access
The dark web presents various threats, including malicious software and computer viruses, posing risks to users’ systems and data security. Users also face the potential danger of government monitoring and surveillance — or scams and fraud, and other activities that can lead to financial loss and identity theft. The Tor browser provides access to “.onion” websites, which are Tor hidden services that you can only access through the Tor browser. You can access these websites without worrying about someone snooping on a Tor exit node, offering more private browsing of what is known as the deep web. I2P is a privacy-focused dark web browser that emphasizes secure peer-to-peer connections.

A Step-by-Step Guide To Access The Dark Web – Trusted Insights From TorConnect
This dark web monitoring will help you track illicit activities and minimize the risks of cyber-attacks. That may seem an extreme way to browse the web, but such protections are increasingly worth considering, says Sarah Jamie Lewis, executive director of the Open Privacy Research Society. Tor greatly enhances anonymity, but if an attacker controls both the entry and exit nodes, they could attempt traffic correlation to link your identity to your activity.
Data Breach Websites
For a limited time, new users who purchase any plan can claim 25% off their first order. The user will have the discount automatically applied after they click on it and check out. This guide dives deep into Tor, explaining how it works, its pros and cons, and how to utilize it to protect your online privacy. Tor Browser already comes with HTTPS-Only mode, NoScript, and other patches to protect your privacy and security. It offers outstanding privacy features and is currently available at a discounted rate.

The core principle of the Tor network was first developed by U.S. Naval Research Laboratory mathematicians and computer scientists in the mid-1990s. The U.S. Army developed “onion routing” to protect intelligence communications online.
It hosts encrypted websites, often used for privacy, anonymity, or illicit activities. There are numerous directories that host .onion links and websites, but you should always exercise caution. ZDNET’s recommendations are based on many hours of testing, research, and comparison shopping.

Can I Access The Dark Web With A Free VPN?
- As a crucial security measure, the Tor Project strongly advises users to verify the digital signature of the downloaded Tor Browser file, regardless of the operating system.
- It allows for encrypted access to any normal website, giving you the ability to surf anonymously.
- People who live under a government that deeply supervises or censors internet traffic eventually get attracted to the dark web.
- It does support whistleblowers by offering them anonymity and secure communication in an oppressive regime.
- Though it still requires being routed through Tor (it is not a deep web browser by itself), it provides a clean, quick, and privacy-respecting base to use for your anonymous browsing sessions.
Avoid fraudulent Tor-like browsers that compromise your online security. The browser is free to download and works on multiple operating systems. The safest and best dark web browsing tool for Android users is the official Tor Browser APK from the Tor Project site.
You can’t open onion links via I2P, and you can’t open I2P links over a Tor network. Whether exploring the hidden internet for curiosity or privacy, these are the best dark browsers. One of the major advantages of using Tor in overly-restrictive countries is that it keeps your online travels private. Unfortunately, some oppressive regimes have figured out a way to block Tor traffic. Tor Over VPN is when you first connect your computer or mobile device to your VPN service and then use the Tor Browser to travel the internet.
What Are Onion Sites?

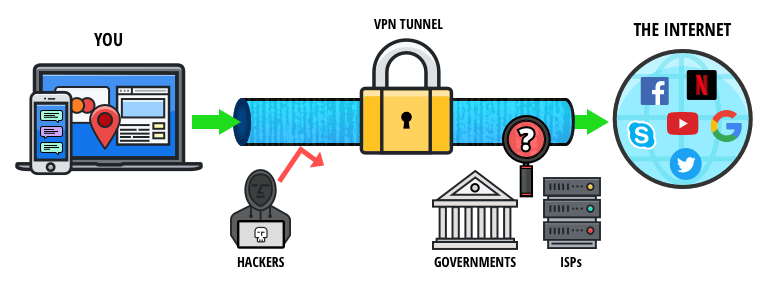
It protects your real IP address even if Tor leaks, is easier to set up, and works with most major VPN services. Open the VPN app and connect to a nearby server before launching the Tor Browser, and that’s it! Protecting your personal information should be your priority when using the dark web.
- Another notable security trick Wasabi uses to verify transactions is the Neutrino protocol.
- At first glance, Tor doesn’t look that different from your regular browser – it has a search bar, lots of quick-launch icons, the peeled onion icon smack in the middle of the screen.
- The dark web allows people to access and share all sorts of illegal and explicit material without judgment or censorship.
- Nonetheless, if whatever you do is deemed illegal in your country, you can get into trouble.
- It would be problematic if someone could open your private email chains through a simple Google search.
Once you have those, there are several ways to tunnel through the dark web. This multi-layered redirection ensures your actions leave no trace, offering a high level of anonymity. For example, randomly clicking a link can land you in extreme content, such as child pornography, which is a serious criminal offense to access. You should review access to your camera, location, and microphone regularly to ensure no website has unnecessary permissions. Additionally, many Internet Service Providers (ISPs) flag Tor usage as suspicious and may block access to the network altogether.



