Their desire came true in September 2018, when the Tor Blog announced the alpha release of Tor Browser for Android. Ever noticed your Android device slowing down, apps glitching, or storage space mysteriously vanishi… Whether you’re a system admin, cybersecurity analyst, or just trying to fix your internet, kno…

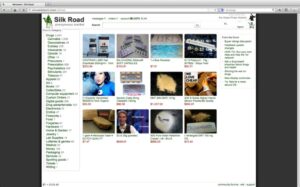
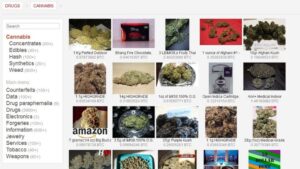
The Full List Of Trusted Darknet Markets:
Apart from the dark web markets that are operating online today, some raided platforms influenced many markets. It has a bidding feature, with new batches of stolen data being frequently added. Some markets are invite-only or have strict registration rules to keep out scammers and law enforcement. It’s been a constant back-and-forth between cybercriminals and law enforcement, with each new site trying to be smarter and more secure than the last. Simply accessing the dark web and using the Tor browser may already raise government suspicion. Unfortunately, it’s also a place where the bad guys can offer their services – for example, hackers or hitmen.
Law Enforcement Operations
It also always uses a secure HTTPS connection, so you’re safer on public Wi-Fi networks too. However, make sure you’re careful which links you click on — some of them lead to sites that contain illegal content and services. This will help you to remain anonymous and secure at all Tor entry and exit nodes. It uses TrustedServer technology on the entire server network to wipe out your data after every session. Since the dark web is a hidden and uncontrolled part of the web, there is a high amount of malware infections present there.

Does The CIA Have An Onion Site?
We’ll focus on secure, ethical practices tailored to cybersecurity professionals and IT leaders. Keybase also offers extremely user-friendly secure chat and file-sharing services through its app. Facebook is aware of attempts by many governments to restrict access to a tool that allows strangers across the web to talk and collaborate freely. While its .onion address doesn’t make it much easier to maintain an anonymous account, it does make Facebook more accessible in places where it’s censored.
How To Change The Tor Browser’s Security Settings On Android

You can pay through Monera and Bitcoin using the escrow system or the traditional market account after making a purchase on this shop. Tor2door Market is among the largest dark net shops you must visit in 2025 if you’ve decided to visit such sites. On average, the marketplace consists of more than 11,000 items and 1000 vendors. Besides this, it supports wallet-less transactions and accepts payments through Bitcoins, Litecoin, Monero, and Zcash. However, you must wait some time to reassess this marketplace because it’s been shut down.
Furthermore, data will help to detect attacks against the network and possible censorship events. The social media giant is also aware of the many attempts by repressive regimes to restrict its access. After all, it enables users to connect and communicate with each other from around the world.
First, Install A Reliable VPN
Tor is a network designed to route traffic through multiple servers. The Tor Browser is a specific web browser, based on Firefox, that utilizes the Tor protocol to enable private browsing. KeyBase combines encrypted messaging with secure file sharing and identity verification. Its dark web version provides the same functionality as the clear web option, while adding Tor’s anonymity layer. Pitch is a dark web-based Twitter/X alternative, providing a secure platform for anonymous discussions and information sharing.
Does Tor Hide Your IP Address?
- From uncensored libraries to secure whistleblowing channels, these platforms can offer benefits difficult to find on the clear web.
- All v3 .onion addresses (the current standard) are 56 characters long and end with “d” to denote the URL version in use.
- The service retains no copies of any data that passes through a ProtonMail account.
- Moreover, due to its popularity, many copycats of the Hidden Wiki exist.
- Naval Research Laboratory mathematicians and computer scientists in the mid-1990s.
Archive.today collects snapshots of websites and archives them for later viewing. If this sounds similar to The Wayback Machine, the concept is indeed the same. However, The Wayback Machine allows website owners to block their sites from being archived, while archive.today does not. A robust antivirus can help block malware and other online threats, even on the dark web.
The platform stood out during my testing for its commitment to anonymity — all messages are fully encrypted and stored on a decentralized network. It’s particularly useful for sensitive communications that need to remain private. Subgraph OS is a Linux-based operating system designed for security, privacy, and dark web access. Built with multiple layers of security and Tor integration, it provides a robust environment to prevent malware attacks and safeguard user data. Instead, download Tor, the most secure and user-friendly option for accessing .onion sites.
These top 10 dark web search engines are important for research, evidence collection, finding hidden resources, intelligence, and various other resources that are not easily accessible. If one tries to visit the dark web with a regular browser, there will be no web pages to visit. Since the dark web is hidden from the surface web, these dark web search engines allow users to explore the concealed part of the Internet. Empire Market is a dark web shop that resembles the AlphaBay marketplace.
Onion sites are websites hidden inside the Tor network, and only the Tor browser can access them. Many popular websites, such as Facebook and DuckDuckGo, have Onion versions, so check if yours has one. If so, it’s better to use the onion address instead of the standard one. To access a dark web address, you must use a VPN and a suitable browser (it should be Tor). The aim is to reduce your online footprint as much as possible, anonymize your traffic, and disguise your location. You could consider the clear or surface web the “top” and visible layer of the internet, easily accessible using a browser such as Safari, Chrome, Edge, or Firefox.
Tor encrypts traffic, masks your IP address, blocks trackers and browser fingerprinting, and doesn’t store a record of your activity. In the image above, (a) is the surface web, which includes publicly visible websites like blogs, shopping sites, and news sites. (b) is the deep web, which consists of sites that require a login to access like email accounts, banking portals, and subscription services. And (c) is the dark web, which is the part of the deep web that isn’t indexed by search engines and requires special tools like Tor Browser to access. Accessing the Dark Web itself is not illegal, but it can become unlawful depending on your activities and the content you access or download.
A favorite of journalists and their anonymous sources, SecureDrop makes it easy to share confidential information without revealing your identity. Many news publications, like the ones listed above, have a SecureDrop on their .onion sites. Pastebins are text sharing services, useful for sending and sharing large snippets of code or text.