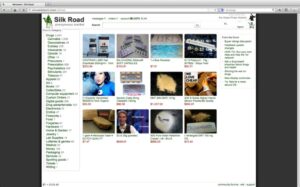
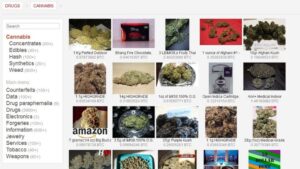
In terms of functionality, I don’t think there are too many differences between regular IMAP, POP3, and SMT services and the stuff you can use to communicate on the dark web. For instance, if you want to buy a laptop or a smartphone, you can try your luck in one of these shops. Sure, you can use other cryptocurrencies if Bitcoin’s not your cup of tea. You should stay away from everything labeled “porn”, “card skimming services”, “PayPal hacks”, “firearms”, “real fake IDs and passports”. Believe me – there are plenty to go around and each and every one of them are being kept under surveillance. Not to mention the fact that you’ll get exposed to some stuff that will definitely make you take several cold showers.
Comparing The Dark Web And The Deep Web
It hosts both legal and illegal activities, offering anonymity but also posing risks like scams and illicit content. In addition, know that while accessing the dark web is legal in most countries, engaging in illegal activities (buying or selling contraband, hacking services, etc.), is illegal everywhere. You should be aware that law enforcement agencies may be monitoring the dark web and that visiting certain websites or engaging in illegal activities can result in criminal charges. You can also check out this ultimate dark web safety guide to browse safely. Safety concerns on the dark web include encountering criminal-run websites offering illegal goods and services, with the added risk of exploitation and theft. Engaging in illicit activities can lead to prosecution, as the law applies equally in this hidden part of the internet.

A Quick Guide On How To Use A VPN With Tor
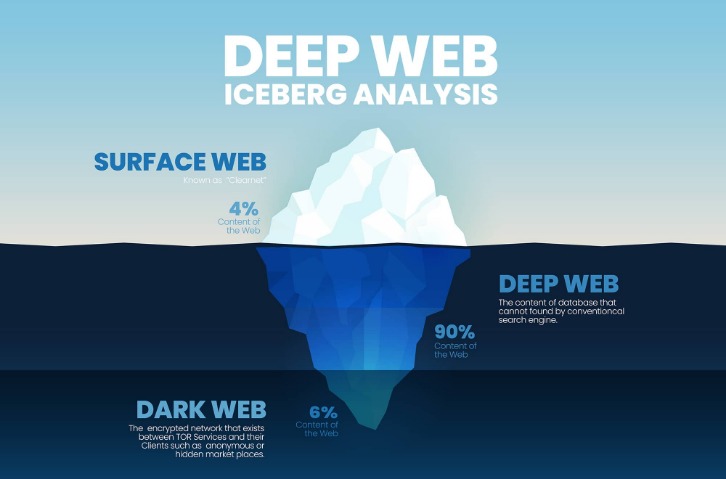
Put simply, there’s a lot more secrecy than the already secret act of using Tor to visit a website on the open internet – for both parties. When you purchase through links in our articles, we may earn a small commission. Install Avast SecureLine VPN for iOS to protect your privacy and keep your data from falling into the wrong hands. Install Avast SecureLine VPN for Android to protect your privacy and keep your data from falling into the wrong hands.
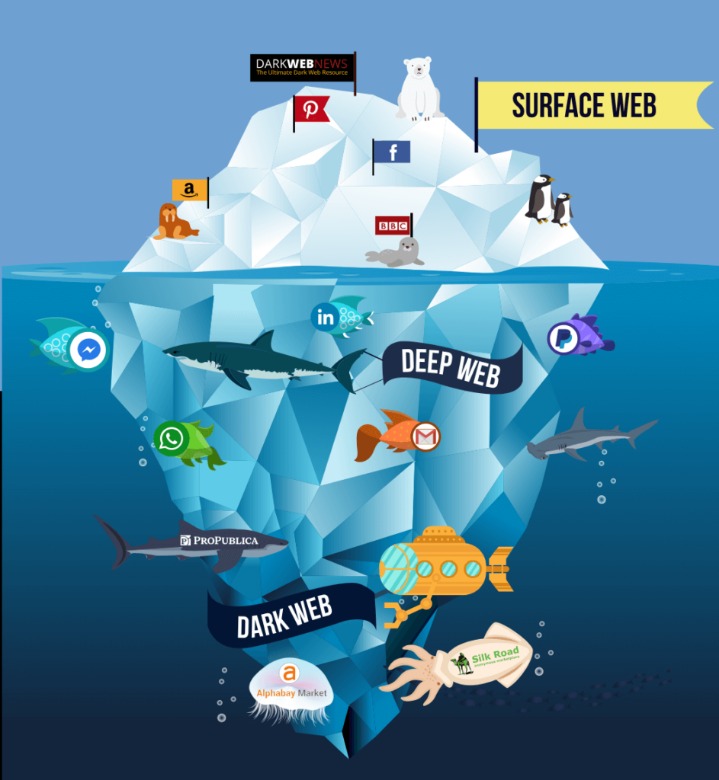
Since you’ve now installed the Tor browser, you can safely browse dark web websites and other (previously) hidden websites. The majority of the users on the dark web use the Tor (The Onion Router) browser. A vast number of URLs have domain endings such as “.onion”, which means that the URLs are only accessible by Tor users. It has been estimated that a large percentage of dark web traffic is related to illegal pornography that includes underage victims. The dark web is a very popular platform for journalists, political bloggers and political news publishers, and in particular, those living in countries where censorship shields most of the internet.
What Boards Want And Don’t Want To Hear From Cybersecurity Leaders
There are also reports of “evil GPT” products sold on dark forums or via private messaging, according to Vishavjit Singh, senior threat intelligence researcher at eSentire. Initial access brokers (IABs) are thriving, selling entry points into corporate environments, which are then monetized by ransomware affiliates or data extortion groups. Ransomware leak sites showcase attackers’ successes, publishing sample files, threats of full data dumps as well as names and stolen data of victim organizations that refuse to pay. Depending on the size of your digital footprint and your online privacy setup, your personal data may be leaking in small drips or flooding onto the Dark Web. As it pools together, hackers use it to fuel other criminal operations, combining details and reusing them for subsequent attacks.
Specialized Data Repositories
Your connection also may be encrypted but if you do something like send an email from your personal account, then anyone with access to your inbox will know that you were online at that time. Unlike the open web, these sites aren’t really worried about being found by on-page SEO tools like web crawlers. While there are Google-like equivalents trying to categorize the dark web, results are spotty. There are some supposed ‘dark web’ search engines like Torch or Haystak is said to have indexed more .onion sites than any other search engine. Deep sites also include company intranets and governmental websites, for instance the website of the European Union.
Friends & Links
Moreover, you need to be more cautious while accessing it, as without proper safety, you can fall into the wrong hands and face serious consequences. Following are important tips you need to remember while visiting this dark part of the web. Dark web forums are very similar to their clear web counterparts in almost every way, except for the content they discuss. Indeed, some began life on the clear web before migrating to the dark web to evade surveillance or censorship. Forums cover the breadth of criminal activity but these examples show there is a particularly thriving community of cybercriminals sharing information, tutorials, access, and exploits.
Stolen Data And Identity Theft
- In fact, there have been instances where attackers controlled hundreds of Tor nodes.
- And just like in real life, using the dark web for criminal purposes is never legal.
- Internet security software like Kaspersky Premium are comprehensive to cover both identity monitoring and antivirus defenses.
- This is one of the reasons why it is always good to hide your IP address.
- Increasingly, privacy-focused coins such as Monero (XMR) and Zcash (ZEC) are being adopted to protect anonymity and make tracing funds difficult for law enforcement.
It is particularly vital for users in countries under oppressive regimes, offering a lifeline for free speech. Despite the dark web’s anonymity, users still need tools to navigate its vast and often confusing landscape. Several dark web search engines have been developed to index and provide access to hidden services. Examples include Ahmia, which filters out illegal content and offers a safer search experience, and Torch, known for its extensive index of dark web sites. By definition, the dark web is the home to the darker corners of the internet. These corners are deliberately concealed from the public eye and require specialized tools and browsers to access, making it more difficult for the average person to explore.
What Are EWallets And How Safe Are They?
The most widely used tool for accessing the dark web is the Tor (The Onion Router) network, which uses a method called onion routing to obscure user identities and activities. Tor (“The Onion Routing” project) network browser provides users access to visit websites with the “. This browser is a service originally developed in the latter part of the 1990s by the United States Naval Research Laboratory. Drugs are typically sold using cryptocurrency to maintain anonymity, and the buyers and sellers are often difficult to trace.

There are also many tools that can be use to monitor the dark web and scan for personally identifiable information and even respond to attacks. As I’ve mentioned, the dark web isn’t just a place of eternal torment, teeming with drug dealers, human traffickers, and a hitman. It’s also used by journalists, advocacy group members, and political refugees in hiding. Reuters, Fox, NBC, CNN – all of them keep open dark web channels to receive anonymous tips from whistleblowers. So, it’s only natural to find ways to keep in touch with your darknet buddies and/or customers.
When browsing through Tor on the dark web, however, the suffix is .onion. It’s fitting because Tor itself stands for The Onion Router, a reference to the multilayered (like an onion’s skin) encryption it uses to keep users anonymous. A repository of sites that can’t be found by traditional search engines, the dark web is as intriguing as it is dangerous. We take a deep dive into what the dark web is and the dangers it poses.
Q4 What Is GRC Score And Does It Factor Dark Web Exposure?
The most prevalent dark web content is child pornography, about 80% of its web traffic, despite being challenging to find. Other porn-related content found on the dark web includes revenge porn and sexualized torture, and the killing of animals. The Dark Web has a social media platform called the Dark Web Social Network (DWSN), which is similar to regular social networking sites. Users can create customizable profiles, have friends, and participate in forum discussions.