Despite its mandate by Congress, the center is not subject to public records laws and operates with little transparency. It repeatedly denied requests from The Times for quarterly and annual reports submitted to the Justice Department, as well as for tallies of imagery reports submitted by individual tech companies. Increasingly, criminals are using advanced technologies like encryption to stay ahead of the police.
What Parents Need To Know About The Darknet
You may also want to consider installing antivirus and anti-malware to protect your home network, and see to it that all your devices are up to date with the latest security features. Understanding online safety and the risks of being online, including grooming and bullying, is vital to keeping children safe online. To access hidden services and to establish anonymity requires a level of skill. Therefore, understanding the motivations as to why a young person is accessing these encrypted parts of the web can tell us a lot and must be taken in context. You might often see news stories about criminal activity involving the dark web, and because of what’s happening in some corners of the dark web, it tends to put off law-abiding companies and users alike. Sections of the dark web are often closed down too, as part of police operations.
Case Studies: Child Sexual Exploitation
- Try playing board games, go for a walk, engage in art activities, or teach them how to cook.
- Pleeeeeaase’ and much more explicit topics, there are also sections on politics and sports.
- There are also services for things like computer-hacking and hitman-hiring.
- While this list is not comprehensive, it is a short overview of the types of activity you might see on Telegram.
Awazon became the successor of the popular AlphaBay market, which the authorities shut down successfully in July 2023. Like any other site of such nature, Awazon Market isn’t free from risks, so be careful while accessing it. You can choose the best darknet (.onion) website that suits you and start surfing. For safer browsing, it is highly recommended to also use a VPN and antivirus software. In addition, make sure they know how to report to CEOP’s Safety Centre if they are concerned about sexual abuse and exploitation online. When people use social media, does it destroy real human relationships?
Best Dark Web Sites: Unseen Onion And Tor Links
Google considers the majority of the content on the entire web highly irrelevant and useless to its users. That’s why such a large percentage (as much as 94%) of the entire web is not returned in Google Search. Did you know that Google only shows you a glimpse of all the websites that actually exist? The last time I checked, it’s estimated that the entire web is roughly 500 times larger than what Google returns in Google Search. CSAM provides a paramount example of how technology can be used in harmful ways. 282 of the open-ended responses explicitly mention the age of children depicted in the CSAM viewed, providing 1637 mentions of age.

Create A Healthy Digital World For Your Child
The shutdown operation, called Operation Pacifier, involved the Federal Bureau of Investigation (FBI) hijacking the site and continuing to serve content for two weeks (from February 19, 2015 until March 4, 2015). During this time, the FBI used a malware-based “Network Investigative Technique” (NIT) to hack into the web browsers of users accessing the site in what is known as a watering hole attack, thereby revealing their identities. The operation led to the arrest of 956 site users and five prison sentences.
Omegle has been the subject of recent viral videos from popular social media influencers including KSI, Charli D’Amelio, James Charles and Emma Chamberlain. Technology is woven into our everyday lives, and it is necessary in many ways even for young children. Young people are spending more time than ever before using devices, and so it is important to understand the risks of connecting with others behind a screen or through a device and to identify what makes a child vulnerable online. Opening the onion links is very easy from the Tor browser, which you need to download and install in advance.
External Links
The police complain that the most urgent reports are not prioritized, or are sent to the wrong department completely. In a 2016 Wisconsin case, Tumblr alerted a person who had uploaded explicit images that the account had been referred to the authorities, a practice that a former employee told The Times had been common for years. The tip allowed the man to destroy evidence on his electronic devices, the police said. Alicia Kozakiewicz, who was abducted by a man she had met on the internet when she was 13, said the lack of follow-through was disheartening. Now an advocate for laws preventing crimes against children, she had testified in support of the 2008 legislation. “We go home and think, ‘Good grief, the fact that we have to prioritize by age is just really disturbing,’” said Detective Paula Meares, who has investigated child sex crimes for more than 10 years at the Los Angeles Police Department.
Child Sex Abuse Material And Abuse Porn Is Prevalent
“Some of those arrested not only uploaded and watched videos but also abused children,” Europol said, while confirming that “the investigation is ongoing,” making it appear likely that more arrests could follow. Arrests spanned the globe, including 16 in Spain, where one computer scientist was found with an “abundant” amount of CSAM and payment receipts, Todo Alicante reported. Police also arrested a “serial” child abuser in the US, CBS News reported. When such operations are taken by LEA, community members of a “taken down” site will “go quiet” become inactive for a number of days.

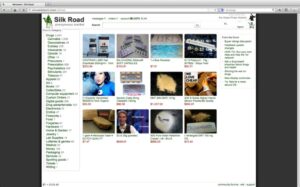
It has been estimated that a large percentage of dark web traffic is related to illegal pornography that includes underage victims. Darknet markets facilitate transactions for illegal goods and services. Silk Road was one of the first dark web marketplaces and it allowed users to trade multiple types of nefarious goods and services, including weapons and identity fraud resources.
The Legality Of Accessing The Dark Web
Our curated list of legitimate dark web sites above offers a safe entry point for first-time explorers. And when tech companies cooperate fully, encryption and anonymization can create digital hiding places for perpetrators. Facebook announced in March plans to encrypt Messenger, which last year was responsible for nearly 12 million of the 18.4 million worldwide reports of child sexual abuse material, according to people familiar with the reports. Reports to the authorities typically contain more than one image, and last year encompassed the record 45 million photos and videos, according to the National Center for Missing and Exploited Children. The darknet provides a haven for those who want to go unnoticed, including those who are keen to break laws.
Child Sexual Abuse Material On The Darknet
Many prominent media sources and journalists maintain a presence on this website location to securely accept documents from anonymous senders. These include big names, such as Al Jazeera, CBC, Forbes, Huffington Post, The New York Times, and many more. When you’re dealing with sensitive information, nothing feels truly anonymous or private. One genuine exception is a site called Keybase, which helps you securely share files and chat online.
Based on result click statistics, we rank the top 26 most visited search engines online on 17 March 2023. To determine whether CSAM is permitted in search results, we test the searches ‘child’, ‘sex’, ‘videos’, ‘love’, and ‘cute’, then study the search results. One of them even states that ‘child porn’ is the number one search phrase. Yet, a user can utilise these search engines to locate other search engines and ultimately locate CSAM through the latter. Even if search engines block sites that directly share CSAM, it is still possible to find other entry points for onion sites that provide links to CSAM websites. With any major Tor website entrypoint, search engine, or link directory, a Tor user is only a few clicks away from CSAM content.
Teens venturing into hidden territories reflects their quest for knowledge, connection, and a sense of individuality. Adolescents naturally test boundaries, but heightened cynicism, increased hostility toward authority, or sudden obsession with taboo topics can signal something deeper. Dark web forums often promote anti-establishment ideas that can shape a teen’s worldview. These shifts in attitude may reflect exposure to harmful ideologies or unfiltered online content. What happens on the dark web, stays on the dark web—at least that’s what teens think. The promise of anonymity allows them to test boundaries, explore alternative personas, or say things they’d never utter publicly.
NordVPN is one of the best VPNs to combine with the Tor browser whenever you want to surf dark sites. It offers top-of-the-line security and fast speeds for a smooth browsing experience on the dark web. ActiveX and Java frameworks are susceptible to being exploited by hackers. Since you are navigating in uncharted territories with all the myriad threats today, you’ll have to disable them in your network settings to stay safe. It’s important to note that although the dark web has many valuable services, it is also a hangout for cybercriminals. However, there are some significant variances in the background despite the similarities.