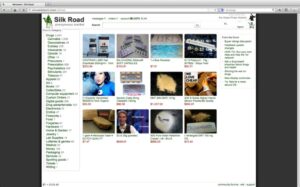
Like other email clients on the dark web, it does not require you to give your personal information. It is a Swiss-based company (privacy-friendly country), and all its tools are open-source, meaning anyone can test its vulnerabilities. Hence, even if you hide your IP address, you aren’t completely secure. For all these reasons, at PrivacyRadar, we strongly discourage using Awazon or any other dark web marketplaces.
How To Choose The Right Dark Web Monitoring Tools For Your Business?
- Tor anonymity comes with a cost since malicious hackers and criminals like to operate in the shadows.
- In fact, whistleblowers have used it to help the FBI or other law enforcement organizations.
- Many people use it for privacy-focused communication, whistleblowing, or accessing restricted information in censorship-heavy regions.
- You can check our guide on the best VPN services to find the right VPN solution to protect your privacy.
When delving into the dark web, maintaining stringent security and preserving your anonymity aren’t just advisable—they’re essential. Threats here range from malicious actors looking to harvest your personal data to hidden exploits designed to compromise your system. A careless misstep can lead to exposure, malware infection, or worse. To protect yourself, it’s crucial to combine multiple security layers, stay vigilant, and adopt best practices tailored for the hidden corners of the internet. Laws pertaining to anonymity and the use of privacy-enhancing tools vary widely from one country to another.
Disgruntled Developer Gets Four-year Sentence For Revenge Attack On Employer’s Network
It provides a safe haven for anyone looking to shed light on wrongdoing or share critical information with the media. ZeroBin is a minimalist paste-bin tool that allows users to share text securely and privately on the Tor network. Tor Metrics highlights that about 22% of daily Tor users come from Russia, while the USA ranks second at 15%. Tor has around 2 million daily users exploring over 65,000 onion sites.
Do I Need A VPN If I Use Tor?
In “safer” mode, JavaScript is disabled on HTTP sites, some fonts are disabled, and all audio and video won’t run automatically, you’ll have to click to play. Slide up to the “safest” level, and as well as those settings, JavaScript is disabled on all sites. If your Social Security number is found on the dark web, take immediate action to protect yourself. Place a credit freeze or lock on your credit reports, monitor your credit reports and financial accounts closely for any unauthorized activity, and consider enrolling in a credit monitoring service. Additionally, contact the Social Security Administration to report the breach and discuss further protective measures. This is in part a response to exit scams, such as what AlphV/BlackCat and other marketplaces have pulled.
- These include crypting services, dropper services, and exploit kits for RaaS and SMaaS, according to Carroll.
- People use it for various legitimate reasons, such as bypassing censorship in restrictive countries.
- And most importantly, be patient as you’ve to sort through a lot of useless results.
- Some users, such as whistleblowers or journalists working on sensitive issues in oppressive authoritarian governments, need privacy to carry out their activities.
- If you choose to pursue exploring any sites on the dark web, you put yourself at risk of being singled out and targeted for hacks and more.
- Darknet is your best source for the latest hacking tools, hacker news, cyber security best practices, ethical hacking & pen-testing.
The New York Times
AI has the ability to accelerate the scale and sophistication of cyber attacks and it’s starting to be incorporated into tools and services on the dark web. Ransomware as a service, stealer malware as a service (SMaaS), and phishing-as-a-service operations are thriving and helping fuel illicit add-on services. There are also myriad support services that help lower the barrier to entry in executing these attacks, or to help make attacks more efficient. These include crypting services, dropper services, and exploit kits for RaaS and SMaaS, according to Carroll. There’s a growing emphasis on scalability and professionalization, with aggressive promotion and recruitment for ransomware-as-a-service (RaaS) operations.
What Are EWallets And How Safe Are They?

Users in countries with strict access and user laws are often prevented from accessing even public sites unless they use Tor clients and virtual private networks (VPNs). To make its journalism more accessible to readers around the world, the New York Times launched its onion service in 2017. You won’t find any “hidden” stories here—it’s the same content as the normal web edition—but users in countries with government censorship will appreciate having a secure way to access it.
Also, you can set a strong password to protect your message and choose how long it will take to expire. Your data is encrypted in the Tor browser before reaching the ZeroBin servers. ZeroBin is a wonderful way to share the content you get from dark web resources. It is a reliable messaging tool where you copy/paste a text or image and send it to your addressee. Blockchain.info (now Blockchain.com) is a popular cryptocurrency wallet and blockchain explorer service (one of the first sites to launch on the dark web).
OnionLinks
Another main upside to this site is that it lets you view the number of .onion links and users on the Tor browser network. Data like this can also help estimate how many people actively access the dark web and how many hidden websites truly exist—you can even tell where the users are accessing from. The invisible web is made up of data and information that is not indexed and cannot be searched for by using traditional search engines. Content includes non-indexed websites, apps, and resources, which can include protected information such as, online banking, specialized databases, non-linked and password-protected websites, and more. It includes media and archives which cannot be crawled and indexed with current search engine technology. Surfshark is a leading virtual private network service provider offering privacy-focused tools.

Thankfully, you don’t need to use your official name or email; just use a fake username (we tested it successfully). The site doesn’t require an email verification, though it offers all the features and security that you want in a dark web marketplace. The Daniel site also had a status check feature that updated users on which sites were active. Unfortunately, the site’s admin could not keep up with the time demands and has taken down the links on the site as of August 2023. It has a vast library of over 1.5 billion indexed pages that lets you find whatever you are looking for. However, the threat of clicking on the wrong link always remains, so be cautious while you use it.

The Hidden Wiki is the dark web’s unofficial Wikipedia, where you can find “.onion” links for many dark web pages, services, and other content. The Hidden Wiki doesn’t discriminate, so if you randomly start diving into the onion sites listed, you may come across objectionable or dangerous material. Torch is one of the oldest dark web search engines, and it’s generally considered one of the safest.
ProPublica — Investigative Journalism News Site
The most commonly used browser for accessing the dark web safely is the Tor browser. Tor is designed to keep your online activity anonymous by encrypting your data and bouncing it through a network of volunteer-operated nodes worldwide. Tor browser also blocks plugins, JavaScript, and other potentially harmful elements by default, enhancing your security while browsing. Enter the Tor network, short for “The Onion Router,” given the many layers of encryption that guard passing information.
Best Onion Sites To Discover On The Dark Web In 2024
This platform allows visitors to anonymously explore the World Factbook, submit information, apply for jobs, and perform any other actions available on the CIA’s main site. I personally recommend Tor over VPN because it’s the safer option — the VPN encrypts your traffic and changes your IP address, so the Tor network can’t see them. That’s helpful because Tor can suffer IP leaks and malicious actors can run Tor servers. Basically, if a Tor IP leak occurs before you connect to the VPN, your real IP address will be exposed.