
Developed by the Freedom of the Press Foundation, the dark web site allows users to privately submit documents and sensitive materials without revealing their identity. The Tor Browser can take you to all kinds of questionable, dangerous, and potentially illegal content. That’s why knowing which dark web websites are safe to visit is vital. Set Tor Browser’s security level to “Safest” for critical dark web activity. This disables potentially dangerous features like JavaScript that could reveal your identity.
What’s The Difference Between Surface Web And Dark Web Search Engines?
When evaluating the onion list’s merits, a strong comparative analysis is essential. While the benefits, such as anonymity and access to unique information, may seem compelling, they must be weighed against the risks of engaging with potentially illegal activities. Understanding this dichotomy is vital for anyone contemplating accessing onion sites, guiding users towards safer and more responsible browsing habits.
Best Free Firewall Software In 2025
First, check out our beginner’s guide on how to use Tor, then come back when you’re ready to get started. Always use a secured device (ideally an isolated virtual machine) and keep downloads off-limits unless you absolutely trust the source. These platforms are harder to track and often rely on decentralized reputation systems. “Hidden Answers” is a community in Darknet, where any user can ask about the use and the investment when buying BITCOIN.
How Can You Monitor The Dark Web Without Using Search Engines?
The forum is notorious for its role in facilitating unauthorized access to networks and distributing malware. Proton Mail is an anonymous email service that operates an onion site. The dark web is a complex part of the internet, and specialized search engines are essential for safely experiencing it.
To access them, copy and paste the hyperlinks provided into the Tor browser. These forums are frequently accessed via the top 10 dark web search engines, serving as essential resources for information and networking. By exploring these categories of resources, users can discover that the dark web’s landscape is more nuanced than popular portrayals suggest.
How To Access The Dark Web Safely In 2025
If you find a link that is not working let us know on our contact page. If the website you are trying to visit has Recommended mark it means it has been verified and is safe to use. Monero’s ring signatures, stealth addresses, and RingCT ensure untraceable trades.
Darkfail – Reliable And Frequently Updated Directory
The dark web and the deep web are often used interchangeably, but they’re two distinct concepts. Search engines on the dark web are a bit of a contradiction because dark web sites by definition are not indexed by traditional search engines. Onion sites (aka Tor sites) are websites only accessible on the dark web; you can’t view them using a regular browser. Their URLs (aka dark web links) have .onion as the domain, instead of the common surface web domains like .com or .net.

We Helped Patch A Chromium Bug That Could Leak Your Real IP — Here’s How
Besides monitoring and improving the network, the data can be used to detect possible censorship or attacks. Due to the privacy-forward ethos of the Tor project, Tor Metrics stresses that the data it collects must not undermine the anonymity or security of the network. In contrast, sites hosted on the dark web can only be accessed via onion routing with Tor, or another dark web browser. Crypto services use various measures to keep cryptocurrency wallets secure and make sure your Bitcoin is safe. Because dark web sites can only be reached with a dark web browser like Tor browser, the best dark web sites, best onion sites, and best Tor websites are all one and the same. And because they aren’t searchable via Google or Bing, onion site lists are important roadmaps to help users find what they’re looking for on the dark web.
OnionLand offers a clean design with a simple user interface that includes search suggestions. The search engine allows you to look for old V2 onion addresses, images, and content on I2P. It also conducts searches across both the clearnet and dark web by leveraging multiple indices, so you can filter searches to focus exclusively on the darknet or span both realms.
Image Hosting — Upload & Share Images
Whether you’re looking for stronger privacy, a simple interface, or a tool designed specifically for hidden services, there’s likely an option that fits your needs. Think about what matters most for your browsing and security, and make informed choices to navigate the dark web safely. It’s specifically designed for privacy, routing your connection through the Tor network to hide your IP address and encrypt your traffic.
You can’t access the dark web without the use of an anonymous browser known as Tor. It routes all your communications via a series of relays operated by individuals across the world. This makes your IP address untraceable and unidentifiable in the process.
- Note that Hidden Wiki links sometimes lead to unsafe content, so be wary about what you click.
- It offers counterfeit documents, financial fraud tools, hacking and malware services.
- Some markets are invite-only or have strict registration rules to keep out scammers and law enforcement.
- Many users value the protection that comes with keeping their identity hidden.
- However, this interconnectedness also comes with risks, such as the loss of privacy and the exposure of personal information.
However, these search engines serve as an entry to the internet’s underbelly. Browsing the dark web is safe as long as you’re accessing legitimate content. Many websites are run by cybercriminals that offer all kinds of illegal goods and services. You might also end up downloading a file or clicking a link which could infect your device with malware. Also, only use .onion links from legitimate sources like The Hidden Wiki.
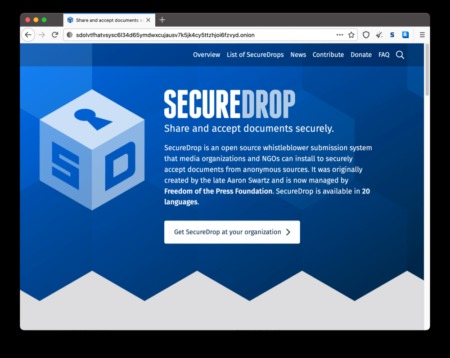
OnionShare is a secure and anonymous file-sharing platform for the Dark Web with open-source code. It works by starting servers locally on your computer that are then shared with others as Tor services. However, it works best in real-time since the file transfers are interrupted if you turn off your system. Similar to Facebook, X (formerly Twitter) also offers a Dark site if you want to access the platform using Tor. Still, you might want to use additional security tools to protect your data when accessing these sites. SecureDrop allows whistleblowers to establish encrypted communication with a news outlet.
Proton Mail’s dark web version provides end-to-end encrypted email with enhanced privacy protection. The service doesn’t require personal information to create an account and works seamlessly through Tor. I found in my tests that all features work identically to the regular version.
- These pages can also help circumvent some forms of government censorship.
- First, rely on community-vetted sources and updated link lists from trusted forums like Dread or The Hub, where users report scams and share verified onion addresses.
- So, search results won’t be based on your browsing history, location, or anything else.
- Also, the platform has a feature of automatic deletion of messages – set a timer and they will be deleted after a set period.
- If you ever land on a Hidden Wiki version with suspicious design, aggressive pop-ups, or broken links, treat it as a red flag and exit immediately.
Why It’s Unique:
If you suspect you’ve clicked a dangerous link, immediately disconnect from the internet, run a full malware scan, and change any passwords that may have been exposed. Cryptocurrency tools help maintain privacy and trust during financial transactions on the dark web. The Wasabi Wallet is a Bitcoin wallet that uses CoinJoin mixing to obfuscate transaction trails, enhancing user anonymity.



