Researchers from the Electronic Frontier Foundation and other groups continued its development and launched the Tor project in 2006 as a tool for journalists, activists, and whistleblowers. Alternatively, users can connect in opennet mode, which automatically assigns peers on the network. Unlike darknet mode, opennet uses a handful of centralized servers in addition to the decentralized peer-to-peer network.
BBC Tor Mirror
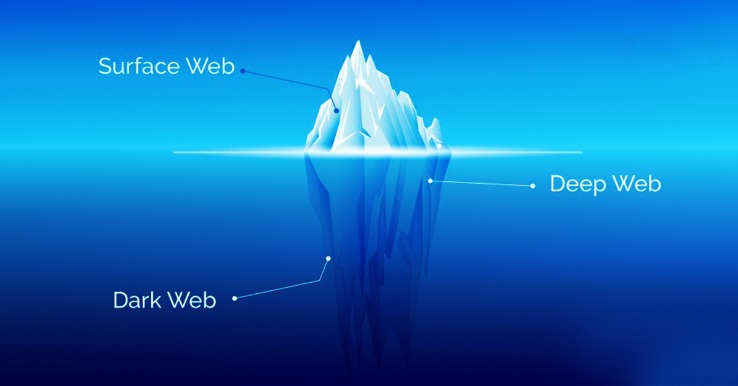
It’s somewhere Google and Bing don’t index, and you need special tools to get to it.
Can I Browse Deep/dark Web Without A Vpn And Just Tor?
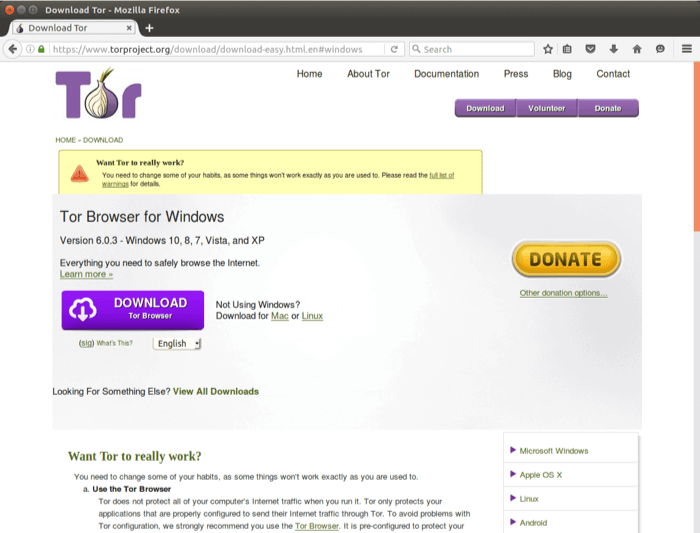
- The easiest way to access Tor is through a special browser known as the Tor Browser.
- Some of the deep web sites do not use standard top-level domains (TLD) such as .gov, .com, .net, etc.
- Not only do you need a dark web browser, you need a dark web search engine too.
- An easy way to find content on the dark web is to receive a link from someone who already knows about it.
Navigating the dark web requires extra layers of privacy, not just because of its content but due to legal scrutiny. The US Supreme Court has indicated that even casual browsing could lead to legal consequences. Setting up I2P requires more configuration on the user’s part than Tor.
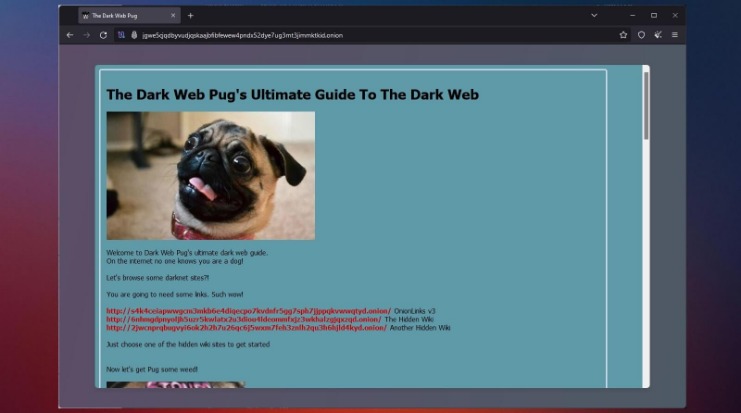
The Hidden Wiki & Co
Though no one should bat an eye just because you’re attempting to access the dark web, keep in mind that in some countries, like the United States, even a simple foray can get you in trouble. Next step – your request will be transferred to Tor entry nod which in turn transfers to one or more Tor relays. Afterwards, your request will be matched with the appropriate website. Tricky, but effective; that’s why it’s, by far, the best method to access dark web content. By using Tor, and especially in combination with a VPN, your internet signal is encrypted, making it invisible to your ISP. Unlike regular browsers that directly connect to websites via your ISP’s DNS, Tor anonymizes your journey by routing your request through several relays before reaching its destination.
Https://g7ejphhubv5idbbu3hb3wawrs5adw7tkx7yjabnf65xtzztgg4hcsqqdonion/
This means that there will be no data to track your activities. With rising online privacy concerns in the current digital age, the Tor network’s anonymity is becoming essential. It is a good way to prevent third parties from tracking online activities.
This includes evidence of any websites you visit, files you open, passwords you use, and even any other devices or networks you connect to. Tails never writes anything to the computer’s hard drive, running only from the RAM of the computer, which is wiped clean when the computer is shut down. Instead, you need to get the Tor browser to access the dark web.
The Future Of Anonymity And Privacy Tools
Just like Google, the dark web has some search engines present on it. Though they have their limitations, most of the time you’ll see irrelevant or spammy links for your search results. You only need to upload your PGP key or let the platform create one. Use it to link your GitHub account, Twitter, Bitcoin address, and Facebook.
Is It Legal To Browse The Dark Web?
It’s where you find both legal and illegal stuff, from hacking tools to drug trade. Successfully navigating this hidden world requires preparation, vigilance, and a thorough understanding of both the technical and ethical challenges at play. From choosing the right networks and privacy tools to avoiding scams and malicious software, every step you take should be guided by caution and informed judgment. The Dark Web remains a shrouded corner of the internet—an enigmatic space where privacy, free speech, criminality, and censorship resistance intersect.

While difficult, tracking is possible if security measures are misconfigured or if users reveal personal information. Combining it with VPN and good digital hygiene improves security. Journalist in India → Uses Tor to access a whistleblowing portal → Submits information anonymously while protecting their identity.
This subreddit exists to debunk urban legends and share real verifiable information from the far reaches of the Tor dark web. Experienced blogger with a strong focus on technology, currently advancing towards a career in IT Security Analysis. I possess a keen interest in exploring and understanding the intricacies of malware, Advanced Persistent Threats (APTs), and various cybersecurity challenges. My dedication to continuous learning fuels my passion for delving into the complexities of the cyber world.
Exiting Safely

Since you’ve now installed the Tor browser, you can safely browse dark web websites and other (previously) hidden websites. From this point onwards, you can enjoy complete anonymity and security while being able to access “.onion” websites and other dark web browser domains. When you install a VPN, all of your activities on the dark web will be hidden from unwanted snoops from your ISP or the FBI. The VPN is a second layer of extra protection, on top of the protection that the Tor network already offers. Accessing the dark web is not illegal in the United States, but naturally, engaging in illegal activity while on the dark web can get you in hot water. There’s legitimate activity on the dark web too, as activists, journalists, and whistleblowers use dark web forums for anonymous communication.
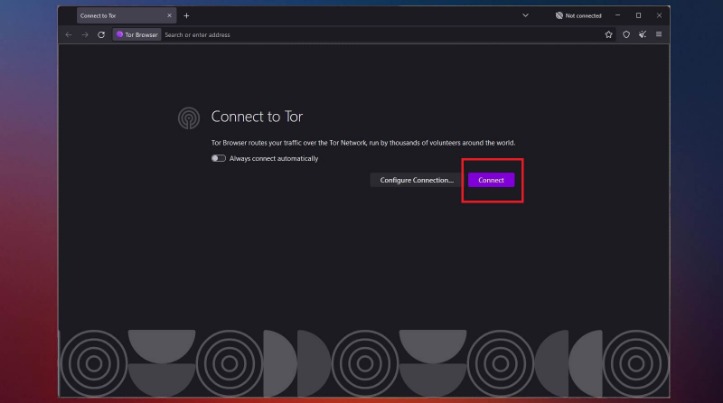
Those layers of encryption and routing activity help to anonymize your movements. Keep in mind though, even the Tor browser isn’t an infallible privacy solution. You can still be tracked at network entry and exit nodes, as indicated by reports that police identified Tor users by surveilling data centers. At this point, Tor will start running and a browser called Aurora will open up.

Start your free trial now and get true browsing privacy today. The dark web, which is what I’m discussing here, is a small subset of the deep web, and refers to websites that are specifically trying to stay out of sight. It’s a part of the internet that’s less regulated and more shadowy, for better and for worse. Traditional proxies are like passing the letter through one person, but onion routing adds layers of encryption at different stops. As digital landscapes evolve, so do the methods of accessing hidden content and maintaining anonymity.



