The dark web is full of unknown and potentially dangerous content. Clicking on links there might take you to illegal or harmful material without warning. You should never trust websites and forums on the dark web with your personal information.
How To Use Tor To Access To The Dark Web
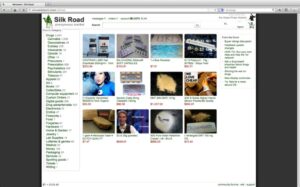
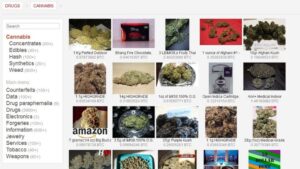
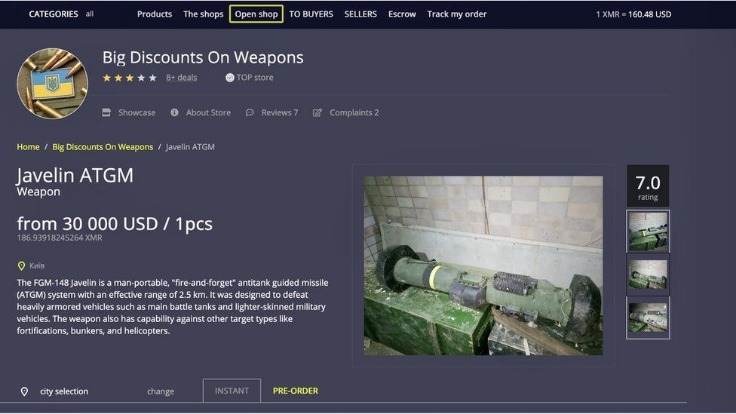
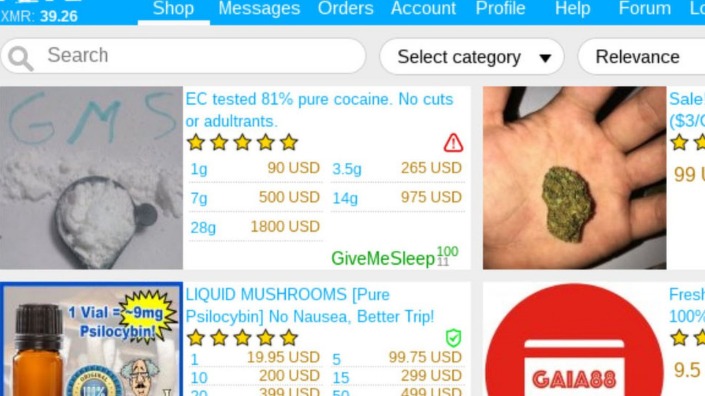
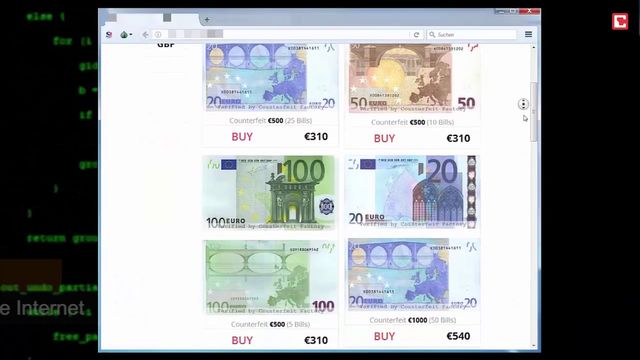
While it might be tempting, remember that downloading such content has serious legal and cybersecurity risks. If you take a quick look through darknet marketplaces, you’ll instantly notice an overwhelming supply of pirated content. We’re talking about even early access to unreleased music, leaked TV episodes, concert footage, and even popular video games before they officially drop. It’s also a marketplace for digital mercenaries; you’ll find everything from solo hackers offering their skills to well-organized groups that take on more complex or high-stakes projects.
Illustration Of Data Processing Passing Through 7,000 Relays On The Tor Network
Most dark web marketplaces use cryptocurrencies like Bitcoin for transactions to help maintain anonymity. Once a buyer makes a payment, it’s usually held in escrow until they receive what they bought. Dark web forums typically look like run-of-the-mill message boards. The real difference lies in what you can post and the poster’s anonymity. Unlike clear web forums, forums on the dark web are almost entirely anonymous and unregulated.
Hidden Answers
You can usually select the location you want to appear to originate from and VPNs will use a collection of servers and relays to make tracing your IP difficult. To access a dark web address, you must use a VPN and a suitable browser (it should be Tor). The aim is to reduce your online footprint as much as possible, anonymize your traffic, and disguise your location.
The History Of Darknet Marketplaces
Install Avast SecureLine VPN for iOS to protect your privacy and keep your data from falling into the wrong hands. Install Avast SecureLine VPN for Android to protect your privacy and keep your data from falling into the wrong hands. The dark net is not quite as lucrative as it used to be and the prices for most of these items or services have gone down in recent years. The hidden nature of the dark web has earned it the nicknames black web and underground internet. However, these names likely conjure up a scarier conception than the real definition of the dark web.
- For this reason, many people prefer to use a VPN to encrypt their connection to the Tor network, thereby preventing their ISP from being able to detect that they are accessing the dark web.
- The deep web is made up of content that search engines such as Google do not index.
- Policing involves targeting specific activities of the private web deemed illegal or subject to internet censorship.
- Mullvad is one of the few providers that offer the VPN Over Tor configuration to access the dark web.
- Data gleaned from ransomware and data breaches is available on the dark web.
- As one of PrivacySavvy’s resident VPN experts, he guides readers on protecting their online information and anonymity.
Avoid Downloading Dark Web Files

You can use the VPN rated #1 for the dark web with no restrictions for a month—great if you want to try this no-log provider’s Onion over VPN servers for yourself. The easiest way to access Tor is through a special browser known as the Tor Browser. You might want to hide your Tor Browser download using a VPN and your existing browser’s private/incognito mode.
Malware Sales
We’ll show you how to access and browse dark web sites, and how using a VPN to encrypt your connection can help you visit the dark web more securely. Understanding how to access the dark web is valuable for IT leaders, cybersecurity experts, and professionals who need to monitor hidden threats or preserve online privacy. By following this dark web access guide, applying Tor browser safety practices, and knowing when it’s safe to browse the dark web, you can navigate responsibly without compromising your security. I2P is a private network built for secure, anonymous communication. Instead of the onion routing Tor uses, I2P relies on unidirectional tunnels and garlic routing, which bundles multiple messages together for better traffic obfuscation.
You won’t be able to access .onion addresses using a standard search engine as they aren’t indexed by crawlers. ZDNET’s recommendations are based on many hours of testing, research, and comparison shopping. We gather data from the best available sources, including vendor and retailer listings as well as other relevant and independent reviews sites. And we pore over customer reviews to find out what matters to real people who already own and use the products and services we’re assessing. It’s perfectly possible to connect to the dark web on mobile, too. In fact, there’s an Android version of the Tor Browser and trusted browser apps on the App Store, too.
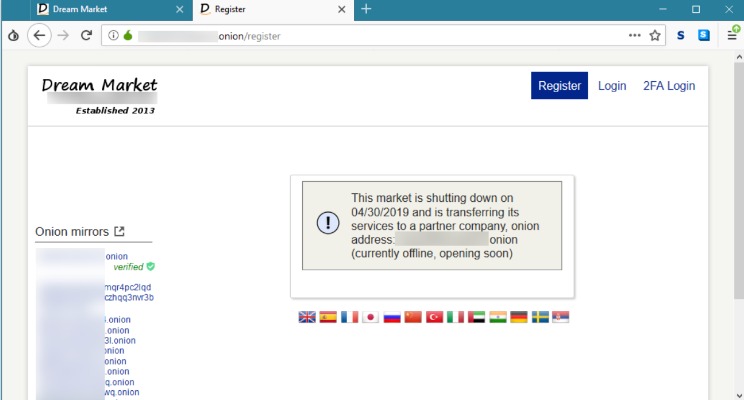
Then, install Norton 360 Deluxe to get AI-powered scam detection to help secure your browsing against online threats. Regular dark web visitors know that it’s possible to exploit the sketchy reputation of the space and the services offered. And though some dark web marketplaces offer user reviews, not all do. Lack of regulation by authorities or other users makes it easy for cybercriminals to carry out scams. Other dark web search engines include Not Evil, Torch, Haystack, and Ahmia.
Proton VPN is part of the Proton family of services provided by Proton Technologies AG. While ProtonMail has a solid commitment to privacy, its location has caused problems for users in the past. In 2021, it was forced by the Swiss courts to begin logging the IP addresses and browser fingerprint information of one of its customers.
Review Of The Best Browsers For Dark Web Access In 2025
This is where Tor websites are located, deemed the ‘dark web,’ and can only be accessed by an anonymous browser. This guide tells you all there is to know about the darknet and how to access both the deep web and dark web safely. There are other ways for spies, hackers or other adversaries to target Tor. Lewis points to the “first contact problem”, when an attacker spots when someone moves from non-private tools to private ones, noting it’s been used to identify whistleblowers. Google doesn’t index these sites, but other search engines do, including DuckDuckGo, and there are lists — including one run by Muffett — so you can find what you’re looking for.
We’ve also previously mentioned the “dark users” that use the dark web for illegal reasons, but the less said about them, the better. Absolutely no one knows who’s surfing on the dark web, who is selling, who is buying or anything like that – as long as you take the correct safety and online privacy precautions. You can also find email messages, online bank statements, and much more information on the deep web – information that is usually private and inaccessible by the public on the surface web. The majority of the web is called the “deep web” (often referred to as the “invisible” or “hidden” web). The deep web is basically all the content that you can’t find using Google or Yahoo search.
Get the latest in privacy news, tips, tricks, and security guides to level-up your digital security. This infects a user’s device and essentially blocks them out of it until they pay a “ransom,” usually in the form of cryptocurrency (so it’s harder to track and recover). Users could accidentally fall victim to ransomware just by clicking the wrong link or downloading a file on the dark web. If you’re in the U.S., you can make use of helpful tools like ExpressVPN’s Identity Defender to inform you if and when any of your data ends up on the dark web. This will allow you to take action right away and reduce the risk of any further damage to your data or identity.