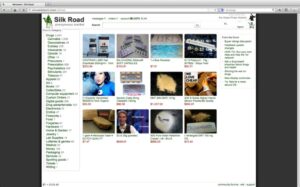
Don’t ever reveal your true identity on the dark web marketplaces because there’s a high chance of hackers and scammers misusing it. Beware of sharing your financial details on the dark web, as this can result in identity theft and your bank account amount being stolen. The Torrez market is one of the biggest dark net marketplaces, also called a community-driven marketplace. It contains a good selection of product listings that range over 35,000 items. The website has an interface and design similar to other dark web shops.
Security And Practical Recommendations
And if you liked this article, follow us on LinkedIn, Twitter, Facebook, and YouTube for more cybersecurity news and topics. Great life advice, but it’s even more valuable where the darknet is concerned. Keep in mind that many criminal organizations use the dark web to communicate or sell merchandise. You may very well end up in the middle of a stakeout that could turn ugly. So, if the website looks fishy, close the tab, and forget about it. You should stay away from everything labeled “porn”, “card skimming services”, “PayPal hacks”, “firearms”, “real fake IDs and passports”.
The Hidden Wiki is a directory hosted on the clear net (also called the “surface web”) that contains a list of .onion links for many of the best dark web websites. Other dark web search engines worth investigating are Ahmia, Torch, NotEvil, and the Onion URL Directory—just type out some keywords for what you’re looking for. Some of these sites can be found through regular web browsers, but you’ll then need to switch over to Tor once you’ve got the onion links you want to follow. The dark web also helps individuals communicate about or sell illegal items such as weapons, drugs, malware, etc.
Hidden Wiki
Here are some of the now-defunct dark web markets that were notorious for cybercrime. Some fake sellers take your crypto and never ship what you ordered, or phishing sites that look like real marketplaces but steal your login info. And then there’s malware—click the wrong link or download the wrong file, and your device could get infected. Others are looking for stolen data, hacking services, or even banned books and political content. For sellers, it’s often about making money while staying off the radar. As of 2020, nearly 57% of the dark web was estimated to contain illegal content, including violence and extremist platforms.
It is a component of Whonix, an operating system that functions as a whole inside a virtual computer. It includes all the essential productivity software, including MS Word and an email client. However, there are some significant variances in the background despite the similarities. For example, Whonix’s virtual workstation machine connects to the internal virtual LAN. It can only interact with the gateway, the most effective method by which the browser protects user applications from learning a device’s IP address. While accessing the dark web using Mozilla Firefox is possible, you must first adjust its settings.
More On How To Stay Safe On The Dark Web
For more information, read more about the most secure email service providers in my other post. Then, simply click the operating system that you are using and download the file. While an iOS version of the official Tor browser is not available, there are Tor-compatible browsers available in the App Store. So, once you’ve activated your VPN and your privacy is secured, it’s time to visit Tor’s official download page.
Abacus Market

This requires your connection to go through multiple nodes and relays, which will slow down browsing on Tor. KEY TAKEAWAYS Whether you are using Android or iPhone, you can easily access the dark web on your ph… Farwa is an experienced InfoSec writer and cybersecurity journalist skilled in writing articles related to cybersecurity, AI, DevOps, Big Data, Cloud security, VPNs, IAM, and Cloud Computing. Also a contributor on Tripwire.com, Infosecurity Magazine, Security Boulevard, DevOps.com, and CPO Magazine. Always use a fake name and a temporary email address when you buy something from the dark net shops.
Tips To Stay Safe When Using The Dark Web
Keybase is an exciting identity service that aims to make it easy for you to link the presence of your online identities together in a cryptographic way. You can upload your PGP key or have the site create one for you, and use it to cryptographically link your Twitter profile, Github account, or Bitcoin address together. Based in Switzerland, ProtonMail is an encrypted email service that is very popular with cryptocurrency enthusiasts. Haystak also offers a premium version that allows advanced search, access to historical content, and email alerts. Finally, you need to enter website addresses to access content on the dark web since you can’t browse by entering a search query as you can on the clear web. Sections of the dark web are often closed down too, as part of police operations.
Invictus Market
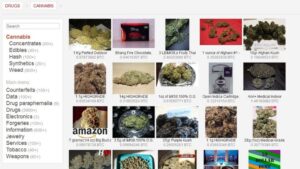
Its intuitive interface and advanced search features make it easy to find local and global products. It stands as a reliable alternative to the defunct Alphabay Market as it continues to position itself as the premier source for advanced privacy-focused digital commerce. Awazon Market is a top-tier dark web marketplace with claims to revolutionize secure anonymous commerce. It offers a wide range of goods and services with robust anti-DDoS protection (with military-grade security protocols) and no JavaScript, ensuring privacy and uptime. This guide outlines different ways of safely accessing dark web stores and the list of reliable dark web marketplaces you can consider visiting in 2025 for research and monitoring purposes. Dark web browsers and search engines do a lot of work to mask user identities, but you’re never completely untraceable.
Cybersecurity Best Practices For Protecting Your Digital Assets
To prevent detection, the program runs user data via a tiered stream before allowing access to the dark web. In due course, the framework was remodeled and made public as a secure browser. No one is hiding here—they’re just guaranteeing that people in censored countries can read the news without being flagged.
- Great life advice, but it’s even more valuable where the darknet is concerned.
- These sites often look basic or outdated, and their URLs are lengthy strings of random letters and numbers.
- No one really knows the size of the dark web, but most estimates put it at around 5% of the total internet.
- Known for its publicity stunt releasing millions of stolen card details for free, BidenCash specializes in credit card fraud and identity theft.
Imagine an underground version of your favorite online marketplace, somewhere hidden, exclusive, and often operating outside legal boundaries. It is similar to an online store, except it’s not the type you’ll find with a quick Google search. From items like drugs, fake ID cards, and hacked bank accounts to more complex offerings like human trafficking, these sites carry all the illegal activities you can think of.

Another private cryptocurrency you’ll find being used is Monero, which prides itself on being untraceable. The dark web, for the uninitiated among you, is a virtual neighborhood beyond the borders of the normal, everyday internet (which includes the website you’re looking at right now). It’s somewhere Google and Bing don’t index, and you need special tools to get to it. Experienced blogger with a strong focus on technology, currently advancing towards a career in IT Security Analysis. I possess a keen interest in exploring and understanding the intricacies of malware, Advanced Persistent Threats (APTs), and various cybersecurity challenges. My dedication to continuous learning fuels my passion for delving into the complexities of the cyber world.
Best VPNs For The Dark Web In 2025
This information can be used to target ads and monitor your internet usage. Also, there’s a vast amount of unsavory content on the dark web, as well as a significantly high number of hackers and scammers looming on the platform. This allows you to use the computer without the risk of corrupting your computer’s normal operating system with viruses or malware. Tails also protects you from possible malware, viruses, or keystroke loggers that may have already infected the computer, as it doesn’t run the operating system already installed on the device. This type of government surveillance applies mostly to countries with environments that are hostile to free speech. On top of that, the installation process of Freenet is rather easy.
There’s a significant risk to dark web users of being exposed to malware (malicious software) infections. There are several programs that hackers frequently use on the dark web. Opennet connections are easier to use, but darknet connections provide more security against attackers on the network. I2P can only be used to access hidden sites that are only available on the I2P network. The last thing you need to do is to start researching vendors and determine what marketplace is a possible vendor to buy the products from.