
Learn how CrowdStrike can help protect your brand and data with CrowdStrike Falcon® Adversary Intelligence. If you discover your data on the dark web, act quickly to minimize the damage and report the incident to relevant authorities to ensure any necessary legal action is taken. That said, many of the actors on the dark web are highly skilled digital adversaries who can easily outmaneuver basic security measures. As a leading cybersecurity vendor, CrowdStrike cautions all organizations and individuals to refrain from using the dark web.
TOR (The Onion Router) is a software that makes it possible for users to communicate and browse the internet anonymously. This is achieved by directing internet traffic through a global network of servers, which conceals the user’s identity and location. The main purpose of TOR is to provide access to the dark web and bypass censorship and surveillance in countries with restricted internet access. On the other hand, the TOR browser is a web browser that uses the TOR network to offer users private and anonymous internet browsing. Navigating the Dark Web offers anonymity and freedom, but it also comes with significant risks that can jeopardize both individuals and organizations. Hidden websites often harbor malicious software designed to steal sensitive information, infect devices, or even deploy ransomware.

Who Created Tor?
Regardless, if you’re looking for something easy to use, try the Tor Browser extension on the Chrome Web Store. Note that despite the name, the extension isn’t affiliated with the official Tor project, so proceed with caution. Tor2Web is a rather popular proxy that works with the Tor network.
How Do I Access The Dark Web?
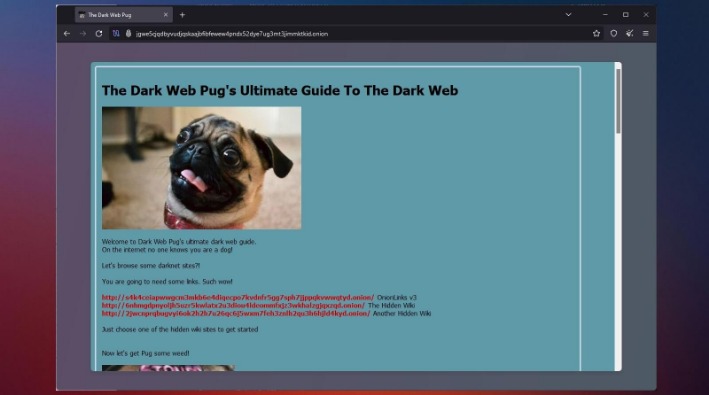
There are several whistleblower sites, including a dark web version of Wikileaks. Pirate Bay, a BitTorrent site that law enforcement officials have repeatedly shut down, is alive and well there. Most e-commerce providers offer some kind of escrow service that keeps customer funds on hold until the product has been delivered. However, in the event of a dispute don’t expect service with a smile.
How To Safely Locate
That’s “a special-use top level domain suffix designating an anonymous hidden service reachable via the Tor network,” according to Wikipedia. Browsers with the appropriate proxy can reach these sites, but others can’t. The terms “deep web” and “dark web” are sometimes used interchangeably, but they are not the same. Deep web refers to anything on the internet that is not indexed by and, therefore, accessible via a search engine like Google.

Another danger lurking in the Dark Web is the proliferation of phishing scams. Fraudulent websites mimic legitimate ones, tricking users into sharing login credentials, financial details, or other sensitive information. These scams not only affect individuals but can also tarnish a company’s reputation. This step-by-step guide is designed to help beginners navigate this hidden part of the internet safely and securely. When viewed through this lens, the dark web’s legality is based on how you as a user engage with it.
Is It Illegal To Go On The Dark Web?
It uses TrustedServer technology on the entire server network to wipe out your data after every session. The dark web is part of the internet that is not indexed by standard search engines like Google, Yahoo, and Bing. It means you cannot access websites on the dark web with regular browsers like Firefox or Chrome. Instead, you need a specific configuration, software, or authorization, such as Tor, to access it. Once connected to Tor, you’re ready to begin exploring the dark web.
Finally, because the dark web routes all traffic through a series of proxy servers, which are operated by thousands of volunteers around the world, the search process is typically very slow. The open web, also called the surface web, includes any public web content that is indexed by search engines. Webpages on the open web will show up in search results on sites like Google and Bing. Though a large volume of traffic visits on the open web every day, it only represents 4% of the content on the internet. That means you can access .onion sites without even opening the Tor browser.
Official Websites And Documentation
- To use the dark web safely, use as many privacy-enhancing tools or programs as you can, and do not identify yourself in any way to anyone for any reason.
- For example, state-level actors can execute traffic correlation attacks, wherein they monitor both incoming traffic at the entry nodes and outgoing traffic at the exit nodes.
- Outside or inside Tor, your traffic is secured 100% of the time.
- You can now start surfing the web while connected to the Tor network.
Many dark websites are perfectly legal and safe to use and, in many cases, are better for your privacy than clear websites. Alternatively, users can connect in opennet mode, which automatically assigns peers on the network. Unlike darknet mode, opennet uses a handful of centralized servers in addition to the decentralized peer-to-peer network. The dark web has no shortage of criminal activity, scams, phishing sites, suspicious links, and malware designed to trick newbies.
Another vital precaution is to ensure that your .onion URLs are correct. Onion URLs generally contain a string of seemingly random letters and numbers. Once you are certain that you have the correct URL, save it in an encrypted note—the Tor browser will not cache it for later. Otherwise, there’s a good chance of falling victim to a phishing scam like this fake Bitcoin mixer. Reddit is also a valuable resource for finding the dark net or deep website you’re looking for. Instead of “.com” or “.org”, dark web addresses can be distinguished by the top-level domain, “.onion“.

Dark Web Sites
Yes, but for .onion sites, you’ll need search engines designed for the dark web like DuckDuckGo’s .onion version. Even with Tor and onion routing in place though, you’re not suddenly completely invisible and free to do whatever you want, without repercussions. Certain details of your traffic can be intercepted at the entry and exit points of the node, by the people running those nodes, if they know what they’re doing and what they’re looking for. You’re also open to threats like end-to-end correlation attacks, so while Tor is a lot more secure and private, it’s by no means completely safe. The dark web comes with its own set of tools and services, including web browsers and search engines (which I’ll get on to in a moment). Part of what makes the dark web the dark web is that you can’t access it through your normal web browser, nor can you look something up on it via a Google search.
Accessing The Dark Web: Frequently Asked Questions
There’s also MultiHop that boosts your encryption, along with MACE which blocks tracking. PIA doesn’t pull punches, so it strikes back against its competition with a proven-in-court no-logs policy, split tunneling, and even port forwarding to diversify its apps. Because of this, not many people are willing to give it a shot except if they have a very good reason. If you’re one of them, good luck finding a provider that supports it. Once you do, that provider will need to configure the entire thing on a specific server first.
Dark Web Threats
Although PrivateVPN has what sounds like a true no-logs policy, it has yet to be independently audited. It will still be able to get the job done if you’re interested in dark web browsing. Apps are independently audited for security and are available for Windows, macOS, Linux, iOS, and Android.
With all of that in mind, you need to tread carefully when browsing, in terms of the sites you visit and the other users you interact with. Bear in mind too that laws about freedom of speech and censorship vary from country to country, which is part of the reason the dark web exists in the first place. Perhaps the best-known thing you can buy on the Dark Web is information collected in what seems like the almost daily data breaches we read about in the news.



