
The platform is also used by governmental cyber departments to identify and track potential criminals or offenders. You can never be sure who’s really behind the other end of the line. Opennet connections are easier to use, but darknet connections provide more security against attackers on the network. The advantages of I2P are based on a much faster and more reliable network. Additionally, I2P doesn’t rely on hidden directories that serve as a resource for .onion domains. I2P can only be used to access hidden sites that are only available on the I2P network.
- That’s why they’re often a popular means of communication among activists, whistleblowers, political organizers, and ethical hackers.
- When your data is found on the dark web, it means that you’ve been compromised.
- Anonymity starts with protecting your internet connection.
- Reuters, Fox, NBC, CNN – all of them keep open dark web channels to receive anonymous tips from whistleblowers.
- However, in June 2025, BidenCash’s relevant domains (around 145) were seized by the US Department of Justice.
- If any user is found not complying with the law, strict and immediate action will be taken against them.
It has an active forum and community along with an extensive user vetting process. Many users mostly rely on a dark web browser and secure Internet access to reach dark websites in that hidden part of the net. On iPhones, you’ll need some specialized apps and a good VPN for added protection.
Key Cyber Threats Facing The Financial Sector In 2025
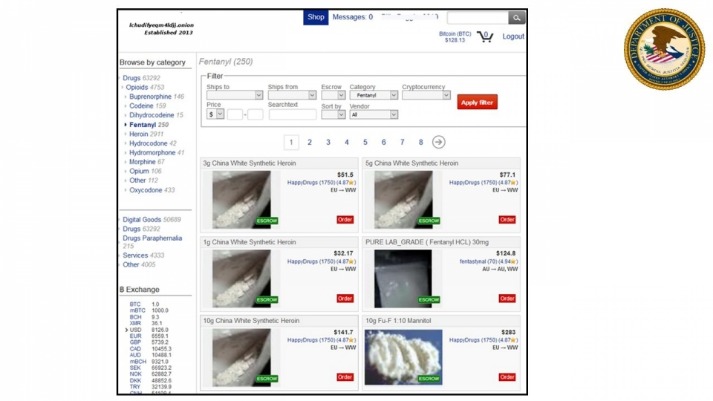
Not only do you need a dark web browser, you need a dark web search engine too. This search engine will get you to the sites you need, though you can also go directly to dark web addresses if you know what they are, as with standard URLs. The Dark Web refers specifically to websites and services hosted inside Darknets. Search engines do not index these sites and use domains like .onion (for Tor) or .i2p (for I2P). When you use it, all the web traffic automatically routes through Tor.
Tips For Safe Browsing:
The dark web is not a place that you can venture into without protection and caution; a slight slip-up can lead to major consequences. Perhaps, the lack of rules and anonymity of the dark web can be tempting, but those are the same things that make it a risky environment. Since 2020, 2easy has sold massive stealer logs with sensitive data like passwords, bank cards, and initial access credentials. It supports operations in multiple languages and operates on both clearnet and Tor. There have been cases of users being identified even after using Tor. However, there are no cases of users being identified when using Tor with a VPN (unless they used a free or fake VPN which shared data willingly with the law).
Don’t Stick Your Nose Where It Doesn’t Belong
Well-known news websites, such as ProPublica, have launched deep websites. Meanwhile, Facebook also offers dark web access to their social network. However, there are several “.onion” search engines like “onion.city”, “onion.to”, and “notevil” that you can use to find suitable marketplaces.
They provide criminals with access to everything they need, from launching attacks to stealing data, etc. Ulbricht faced several serious charges, including distributing illegal drugs, running a criminal enterprise, hacking, trafficking fake IDs, and money laundering. In the end, he was sentenced to life in prison for running one of the largest and most scandalous dark web cases in history. The marketplace supports multiple payment methods, including Bitcoin (BTC), Litecoin (LTC), and Cryptocheck.
#5 Can I Access Darknet Markets Without A VPN?
While this topic may seem distant for most people, understanding how these spaces operate is crucial. It helps us stay more vigilant, better protect ourselves, and make informed decisions online. This market specialized in selling marijuana related products and magic mushrooms, with no “hard drugs” for sale.
Cyber-Attacks And Scams
Given the explosive growth of these markets, organizations must prioritize proactive threat monitoring. Axis Intelligence provides dark web surveillance solutions that help businesses identify leaked credentials, fraud attempts, and malware risks before they escalate. The other coins aren’t always accepted, and even when they are, they aren’t the most privacy-friendly.
Step 2: Choosing The Right VPN Server
On average, each active market in 2019 collected more revenue than those active in any other year, apart from during the height of Silk Road’s heyday in 2012 and 2013. Scammers prowl the dark net, launching fake storefronts that vanish overnight, often with their victims’ money. In 2017, a global police operation brought down AlphaBay, the dark web’s largest illegal marketplace, shaking the underground economy. It’s a lifeline for activists, whistleblowers and journalists seeking safe spaces to connect and speak freely. Social platforms buzz with anonymous conversations, even as law enforcement hunts through digital shadows to crack down on criminal rings.
Supported crypto currencies are Bitcoin, Bitcoin cash & Ethereum. To know about listed items at Tochka, you need to create an account here. To access listed items at The Open Road, you need to create an account here.
Many of these markets operate internationally, and some have certain specialties. To avoid immediate shutdown, the servers hosting DNMs must be in countries with lax legal regulations. This means the server admins must pay significantly higher hosting fees than they would on the clearnet, for less reliable service. As I’ve previously said, it’s a good idea to keep your interactions with the dark web to a minimum, unless you can absolutely trust the people you’re dealing with. You’ll often see a sign in stores that says “look, don’t touch,” and it’s not a bad adage to bear in mind as you navigate around the dark web. The dark web, for the uninitiated among you, is a virtual neighborhood beyond the borders of the normal, everyday internet (which includes the website you’re looking at right now).
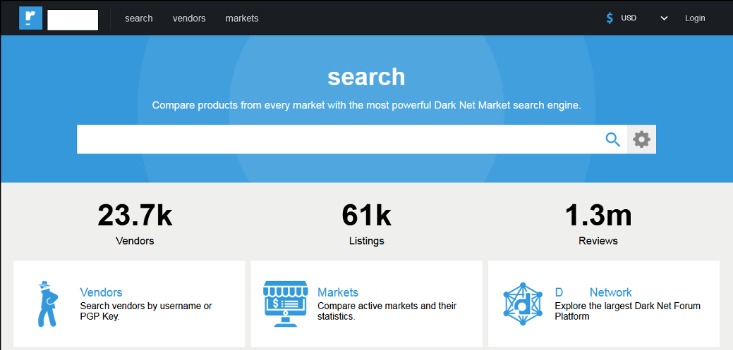
Market Value And Popularity
This means your ISP can’t see that you’re accessing the dark web (or indeed, the specific sites you’re accessing). When you’re on the dark web, you can unknowingly be taken far beyond just places of selling illegal substances or stolen data. You can unintentionally see the explicitly violent and distressing content that is almost always censored or blocked by the reputable “surface” web domains. So, you can come across images, photos, videos, or chatrooms with extreme violence, exploitation, or other disturbing stuff. This kind of content can be mentally scarring, and after such dark web and black market browsing, you can end up with a deep psychological trauma.
Hshlpewgid57veduk7k6d6rt2rmyl5d4juif3ncb5oqc6ko6qdkas4id – Marketplace – DeepSea Marketplace allows the trade of almost everything. Already boasts 4,000+ registered users and 1000+ active product listings. “Pay-per-order” isn’t available, and advance deposits required to the marketplace wallets. Each deposit goes through its internal mixer, and is charged at 0.3%. DeadDrops available, instant offline pickups via the marketplaces. Incognito’s all about keeping things easy and safe—perfect if you’re avoiding street buys.
Such data includes medical records, financial information, research papers, private forums and networks, and other content. Other dark web search engines worth investigating are Ahmia, Torch, NotEvil, and the Onion URL Directory—just type out some keywords for what you’re looking for. Some of these sites can be found through regular web browsers, but you’ll then need to switch over to Tor once you’ve got the onion links you want to follow. The Deep Web includes all content not indexed by search engines.This isn’t necessarily illegal—it’s just private or restricted. Using TAILS is yet another security measure that protects your online identity on the dark web.
Pixel Privacy believes in digital privacy and does not believe in using it for heinous and/or illegal activities, and so the focus of this article will be on legal activities. The content of all these pages is stored on Google’s servers, but it’s mostly outdated, old content; smartphone app content; journals; court records; private social media profiles, and much more. The Onion Project, or TOR is the predominant anonymous computer network.



