Unlike regular websites, .onion sites have complex, hard-to-remember URLs that you can’t find using regular search engines like Google. These malicious actors exploit the anonymity the dark web provides to develop and distribute sophisticated malware that bypasses traditional antivirus protection. As a result, individuals and organizations face heightened risks of falling victim to scams, data breaches, and financial loss. The primary purpose of accessing the dark web is anonymous browsing for activists and whistleblowers, but some people misuse this anonymity for illegal reasons. It is where the dark web becomes dangerous, and with no regulations, it becomes riskier to access without using a protective tool. The cybercriminals are scattered like landmines all around the dark web.
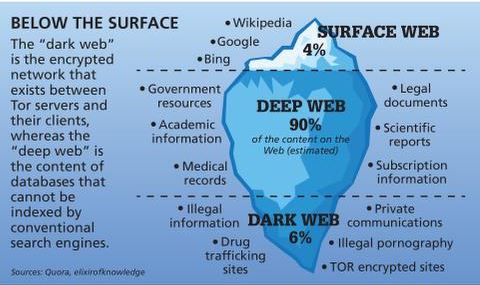
It’s not mysterious or spooky; it’s home to everyday things like scientific research, medical records, private financial information, and secure communications. For professionals in various fields, searching the Dark Web for information is a valuable tool. However, maintaining ethical conduct, respecting legal boundaries, and using encryption and anonymity tools to protect one’s identity are paramount. While you can find interesting websites there, the dark web is a primarily unregulated place where hackers lurk about, selling and buying malware tools and services.

How To Access The Dark Web On An IPhone
Darren Guccione is the CEO and co-founder of Keeper Security, the world’s most popular password manager and secure digital vault. Keeper is the first and only password management application to be preloaded with mobile operators and device manufacturers including, AT&T, Orange, America Movil and HTC. Exploring the Dark Web on your phone can be an intriguing and eye-opening experience, but it is crucial to approach it with caution, respect the law, and prioritize your safety. The Dark Web, with its hidden networks and anonymous browsing options, offers a unique platform for privacy enthusiasts, activists, and individuals seeking uncensored information. However, it is also home to illicit activities and potential dangers that can pose risks to unsuspecting users. The dark web, an even more puzzling sublayer, exists within this hidden world.
If you make use of a password manager, then it may come with a feature that monitors the dark web for mentions of your email address and password, or any other personal details. It’s something built into the password management services offered by Apple and Google as well, so you don’t need to trawl through data leaks manually yourself. Individual sites on the dark web look much like they do on the regular web, though a lot of them are a bit more rough around the edges. (Presentation and polish isn’t quite so important on this part of the internet.) Click on any website link, and it’ll appear on screen, with its address at the top.
Step 2: Switch To A Dark Web Search Engine
NordVPN offers a 30-day, no-risk trial subscription when you sign up on this page. This provides a full month’s access to all of the features of the #1 VPN for the Dark Web. This is an excellent way for Dark Web users to provide additional privacy protection when accessing the Dark Web. Data gleaned from ransomware and data breaches is available on the dark web.
What To Do If My Phone Number Is On The Dark Web
Most dark web leaks happen when users skip basic safety steps or reveal too much without realizing it. Use the tips below to patch common blind spots and avoid easy-to-make mistakes. The biggest drawback of using a VPN over Tor is that your ISP will get to know that you’re using the Tor network, which might raise some red flags. The Tor is a changing proxy overlay network that includes Tor bridges to keep your connection hidden. They are the special secret servers that are helpful to people in oppressive regimes; as the Tor relays are not listed in the public directory, you can remain safe from ISP surveillance.
Many experts advise against using third-party mobile browsers that utilize the Tor Network. If you come across suspicious links, you should avoid clicking on them. It’s important to verify the legitimacy of a website before interacting to protect your personal data and security. Forest VPN adds an extra layer of security by encrypting your internet traffic. It ensures your activities remain untraceable, providing peace of mind. Plus, its battery-saving technology means less CO2 generation, aligning with eco-conscious values.
Tor allows users to browse websites anonymously by bouncing their internet connection through multiple relays across the globe, making it difficult to trace their activity. If you connect to your VPN and fire up Tor Browser, you’re using Tor over VPN. All your device’s internet traffic first goes to the VPN server, then bounces through the Tor Network before ending up at its final destination. Your ISP only sees the encrypted VPN traffic and won’t know you’re on Tor. A logless VPN, which doesn’t store any traffic logs nor session logs is highly preferable.
Accessing the darknet on an android device is not as complex as it may seem. The Dark Web, Darknet, and Deep Web are distinct parts of the internet, each defined by its accessibility and the level of anonymity. The Deep Web is the vast part of the internet not indexed by search engines, encompassing everything that doesn’t appear in search results. This includes mundane things like private databases and paywalled sites.
For Android Users
With rising curiosity around hidden corners of the internet, many professionals wonder, “how to access the dark web” safely. From cybersecurity researchers to IT managers, understanding how to navigate the dark web can help monitor cyber threats, protect sensitive data, and investigate cybersecurity incidents. Other dark web search engines worth investigating are Ahmia, Torch, NotEvil, and the Onion URL Directory—just type out some keywords for what you’re looking for. Some of these sites can be found through regular web browsers, but you’ll then need to switch over to Tor once you’ve got the onion links you want to follow. A VPN encrypts your internet traffic and masks your IP address, providing an additional layer of privacy and a secure pathway to access the Dark Web.
Is Tor Free On IPhone?
The last thing you need to do is to start researching vendors and determine what marketplace is a possible vendor to buy the products from. That means that when Tor is compromised, or perhaps there’s a new vulnerability exploit in the Tor network, a VPN will still protect your privacy. The compromised Tor exploit might trace back to you, but then again, your VPN will lead it somewhere else – which makes it impossible to be traced back to you. It’s important to arm yourself with a good VPN (Virtual Private Network) when you want to enter the dark web to protect your privacy and anonymity. There are a number of services and tools available on the dark web, many of which can be used for nefarious purposes.

Install The Tor Browser On Android
When you purchase using links on our website, we may earn an affiliate commission at no extra cost to you.
Why Use Android To Access The Darknet?
To improve your security, always use a VPN, configure your Tor Browser to the highest security settings, and avoid downloading files or providing personal information. However, engaging in certain activities, such as purchasing illegal goods or services, is against the law. Remember, while the dark web can be a valuable resource, it’s not without risks. To help you make educated choices about cybersecurity to keep you (and your data) safe and secure, by providing detailed, accurate, and practical information based on thorough testing. Unlike Tor, I2P is designed for peer-to-peer services like file sharing, email, forums, and even decentralized websites — all within its own closed network. Its distributed nature makes it more resistant to central points of failure.
- The Tor network was created to open safe communication channels for political dissidents and American intelligence operatives around the world.
- As always, protect yourself from online threats with mobile Android security or iOS security software.
- You can easily set up Tor on your iPhone, but you do need to use Orbot for it to work.
- It’s important to discern the difference between the technology of the Dark Web and the activities that occur within it.
- There are also several legitimate companies and entities that have a presence on the dark web, and private users may have legitimate reasons for accessing the dark web as well.
We’ve also previously mentioned the “dark users” that use the dark web for illegal reasons, but the less said about them, the better. The purpose was to protect U.S. army soldiers and agents in the field, but also politicians who held secret meetings and conversations, which contained the highest security measures. The dark web addresses are a randomly-scrambled sequence that generates URLs, mostly hard to remember ones. For example, the URL of Silk Road is rather unintelligible and may look something like “gan4arvj452janndj4a76.onion”. But human trafficking, illegal pornography featuring underaged victims, money laundering, and assassinations are also examples of the darkest corners on the dark web. The majority of the web is called the “deep web” (often referred to as the “invisible” or “hidden” web).
- As Orbot and Orfox are two of the most reliable apps, most of the users prefer them.
- If you want to dive into the darkest depths of the web, you’ll need to hitch a ride on the Tor browser—but should you?
- Opinions expressed herein are those of the authors and not necessarily those of Analytics Insight, or any of its affiliates, officers or directors.
- Discover how to safely navigate dark web links for Android users with essential tips and tools for secure browsing.
- However, it’s important to note that some content on the darknet may be illegal or inappropriate.
- To help you make educated choices about cybersecurity to keep you (and your data) safe and secure, by providing detailed, accurate, and practical information based on thorough testing.
While it’s generally safe to use, dark web activity can be detected at the entry and exit nodes of the Tor network. By following the guidelines outlined in this guide and exercising caution, you can explore the Dark Web on your Android phone while minimizing potential risks and maximizing your security. Stay safe, be mindful of your online activities, and respect the boundaries of the law as you venture into the depths of the Dark Web.



