Antivirus will ensure that any viruses or malware downloaded from the dark web are removed. Understanding how it works, from onion routing to decentralized hosting, is key to navigating it safely and responsibly. The dark web offers powerful privacy tools, but it also hosts real dangers—from malware and phishing to deanonymization and law-enforcement traps. You need a full-spectrum security mindset that combines technical setup, behavioral discipline and financial hygiene. The BBC’s Tor mirror (bbcnewsv2vjtpsuy.onion) delivers global news to audiences in countries that block the broadcaster’s regular site. In short, the deep web is about restricted access, whereas the dark web is about engineered anonymity.
How To Get On The Dark Web Using Tor Browser
- You should also avoid clicking on suspicious ads or pop-ups, as they may contain malware or lead you to scam sites.
- Such sites include blogs, gaming sites, social media, and super-encrypted email platforms.
- Tor Bridges or a VPN will help you to use Tor privately, as your ISP (Internet Service Provider) will not see that you’re connected to a Tor node.
- Whether you’re browsing forums, grabbing files, or just exploring the unknown, your connection needs to be private, encrypted, and airtight.
- There are several ways to protect your online activities from being tracked.
You will have to manually configure it to connect to the Tor network. Its strongest appeal is that it has strong privacy defaults, making it usable for daily use that can be expanded upon. It is perhaps the most secure way to run applications anonymously. If you want a strong setup that has no leaks, Whonix might be the best dark web browser solution on the market. Subgraph OS is more than a browser; it is an entire operating system focused on security. The built-in browser is hardened for maximum privacy, and it is integrated with the OS’s security features.

Step 2: Download And Install Tor Browser
From there, you can begin exploring, but you’ll need direct links to access dark web sites, since search engines like Google don’t index them. You will never know when you stumble upon illegal materials, inadvertently download malicious software, or expose yourself to identity theft. But if you must visit the dark web for ethical reasons, here are some safety precautions.
Can I Use Normal Search Engines On Tor Browser?

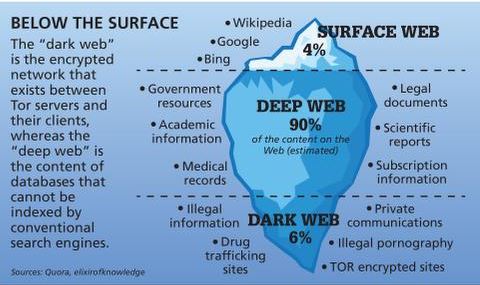
While the term “deep web” might evoke images of hidden, secretive content, most of it is just routine data stored on private networks. Imagine a vast, shadowy expanse of the internet where the usual search engines dare not tread — this is the dark web. It’s a hidden layer of the internet, shrouded in secrecy, that you can’t access using traditional search engines like Google or Bing. Unlike the websites you browse daily, the dark web requires special tools to access and explore. It’s like a secret alleyway (say Diagon Alley from “Harry Potter”) in the sprawling city of the internet, known only to those who seek it out. The dark web is a part of the internet that isn’t indexed by search engines.
One of Daniel’s impressive features was the built-in functionality that showed whether a particular dark website is online. After more than a year of no updates, the site admin shut it down, reasoning that he couldn’t keep the list of onion links up-to-date. If the VPN connection fails, the automatic kill switch will kick in, temporarily breaking your traffic. The Camouflage Mode is intended for people living in countries with heavy internet censorship, like China. It will make your VPN activities seem like normal traffic, so you can use an uncensored internet. However, this feature is only available on iOS, Android, and Windows.
How Can I Increase Security While Using Tor?
While Tor is the most common method for accessing the dark web, I2P and Hyphanet offer alternative options for secure and private browsing. Let’s go through the setup process for each, as well as how to use them effectively. In this setup, the VPN connection acts as a middle layer between your device and Tor, routing your internet traffic through the VPN before it reaches the Tor network.
Is There A Tor Browser For Android?
The Experian Smart Money™ Debit Card is issued by Community Federal Savings Bank (CFSB), pursuant to a license from Mastercard International. To view important disclosures about the Experian Smart Money™ Digital Checking Account & Debit Card, visit experian.com/legal. The value of the information can vary greatly depending on what’s being sold. Full profiles, or fullz, may come with a name, Social Security number, date of birth and account numbers and could cost around $8 to $30 each. Complete medical records can be particularly valuable to identity thieves, and may go for up to $1,000. Cryptocurrencies, such as Bitcoin, are the preferred means of payments as these also help keep buyers and sellers anonymous.
Tor Over VPN Vs VPN Over Tor: Which Should You Use?
These sites can be used by both hackers and individuals looking to exploit vulnerabilities. These are platforms where leaked or stolen data, including personal information, passwords, and credit card details, are bought and sold. They often provide access to vast amounts of compromised data from previous hacks or breaches. Some dark websites serve as platforms for whistleblowers to anonymously share sensitive information.
Other sites explicitly block search engines from identifying them. These sites are a hybrid tutorial-underground where wannabe hackers ask questions and professionals sell their services or stolen data. With the onion browser, you can access ordinary HTTPS websites on the web.

Only a tiny portion of the internet is accessible through a standard web browser—generally known as the “clear web”. With over 15 years of experience in content creation and digital publishing, he knows how to craft informative, useful content, with thorough research and fact-checking to back it up. He strives to make complex cybersecurity topics accessible and understandable to the broadest audiences. In his spare time, Michael likes writing fiction, reading murder mystery novels, and spending time with his family.
Some services are genuine; you can get what you want at an agreed fee. Furthermore, it’s critical to understand that Whonix is not a stand-alone browser. It is a component of Whonix, an operating system that functions as a whole inside a virtual computer.

The banks, lenders, and credit card companies are not responsible for any content posted on this site and do not endorse or guarantee any reviews. Experian is a globally recognized financial leader, committed to being a Big Financial Friend—empowering millions to take control of their finances through expert guidance and innovative tools. As a trusted platform for money management, credit education, and identity protection, our mission is to bring Financial Power to All™.



