
Before accessing the dark web, install strong security software to help keep your device protected. The Tor Project says that of the 2 million people using Tor every day, only 1.5% of them are accessing hidden or dark websites (that’s 30,000 people). Most dark web websites are in English; according to one estimate, a staggering 78% of information on the dark web is in English. When using Tor, your traffic will never reach its intended destination directly, as it would on surface web browsers.
Hidden Answers
This node decrypts your traffic and it reaches the destination i.e. the website you want to visit. You need a special browser (Tor) and all of these websites are intentionally obscured. So, to clarify again, this tutorial will cover how to access the dark web privately and safely – not the deep web. You can go on the dark web safely, use legal sites, and enjoy the experience without worries. In this tutorial, we’ll explain how to access the dark web in complete privacy and cover a few more important factors to consider before starting.
Ways Small To Midsize Businesses Can Stay Safe In The Cloud
Both rely on a peer-to-peer routing structure and layered encryption to make browsing private and anonymous. A VPN allows a user to encrypt all internet traffic traveling to and from his or her device and route it through a server in a location of that user’s choosing. A VPN, in combination with Tor, further enhances the user’s security and anonymity. That information is hidden simply because most users won’t find it relevant. Much of it is tucked away in databases that Google is either uninterested in or barred from crawling. Dark net websites are called “Tor hidden services”, and they can be distinguished from normal websites by their URLs.
- My favorite antivirus in 2025 is Norton, which scored a 100% protection rating during my tests (handily beating the built-in protections on my devices).
- In any case, it can be used for any dark web activity thanks to various privacy features.
- You can choose 256-bit for maximum protection or 128-bit if you want a faster connection.
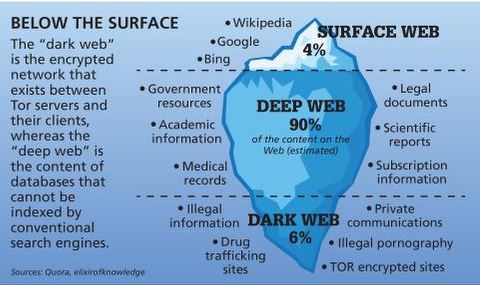
- The dark web (often referred to as the “dark net”, “black web”, or “black net”) is a small section of the deep web that is hidden and kept inaccessible to regular internet users on purpose.
- Tor over VPN requires you to place some trust in your VPN provider but not your ISP, and is best if you want to access .onion websites.
Use A Dedicated Browsing Machine
The dark web is like the mysterious basement of the internet — dimly lit, a little spooky and filled with stuff you probably shouldn’t touch. But don’t let its reputation fool you; the dark web isn’t all shadowy figures in hoodies plotting world domination. To understand how this is possible, we need to see how the web has many layers, and not all content is publicly available from a search engine query. The dark web’s origins are often traced back to March 20, 2000, with the launch of Freenet, a peer-to-peer sharing network designed to prioritize anonymity.
- Norton 360 Deluxe provides a comprehensive suite of protection that can help block malware and dangerous links in real time, and even detect scams using cutting-edge AI detection.
- This enables individuals to form groups and only share content in a highly anonymous network of darknet users who they know.
- This will allow you to take action right away and reduce the risk of any further damage to your data or identity.
- Your access to illegal content, even if it is unintentional, can violate laws in many countries.
However, it also offers significant advantages, especially in terms of privacy and security. For individuals living under oppressive regimes or anyone needing to communicate away from the watchful eyes of surveillance, the dark web is a valuable tool. A substantial portion of users turn to the Tor browser for its promise of anonymity, while others seek the additional security it provides. Curiosity about what the dark web has to offer also drives about one-third of its users. Now that your connection is active, it’s encrypted and untraceable by your internet provider. Everything you do is protected by NordVPN, which is key to accessing the dark web and enjoying it privately.
Connecting To The Tor Network
Remember to update the Tor Browser regularly to ensure you have the latest security patches, and scan your computer for malware regularly using antivirus software. To properly peel back the internet’s layers, you need a tool that provides layers of encryption to hide your activity. Those layers of encryption and routing activity help to anonymize your movements. Keep in mind though, even the Tor browser isn’t an infallible privacy solution. You can still be tracked at network entry and exit nodes, as indicated by reports that police identified Tor users by surveilling data centers.
Understanding The Risks

There are multiple search engines on the dark web that can help you find what you’re looking for. DuckDuckGo’s no-track dark web search service can be accessed in the Tor browser and is an excellent resource for information about the dark web. Social networks, such as Facebook, have created dark web versions of their sites to address privacy problems related to their surface web versions. ExpressVPN had created a .onion version of its website to allow greater privacy and anonymity for Tor browser users.
Step 7: Use Additional Security Tools
Whether you are purely curious or have specific reasons for venturing into the Dark Web, knowing the ins and outs will help you navigate this hidden realm more effectively. To access the Dark Web, users need to use a specialized browser, such as the Tor Browser, which connects and communicates with the Tor network. The Tor Browser ensures that users can access and navigate websites within the Dark Web while maintaining their anonymity. Illegal content on the dark web extends beyond tangible goods to digital products like malware, hacking services, and counterfeit documents. Law enforcement agencies have increased efforts to shut down these markets.
It aims to advance research on terminal illnesses like cancer with access to unbiased scientific publications. Regardless of being a business, parent, or any other user of the web, you’ll want to take precautions to keep your information and private life off the dark web. The use of the dark web usually means that you are attempting to engage in activity that you could not otherwise carry out in the public eye. Explore this FAQ section to get answers to some common queries about this hidden part of the internet.
Do I Need A VPN To Access The Dark Web On My Phone?
While the iOS solution is not an official one, the Tor Project links to it, providing the browser its tacit approval. We’ve also looked at how Tor allows users to access the dark web, and we’re now aware of the resources and dangers that await us there. We’ve found that Tor is an excellent way to keep your internet browser-based online activities undercover, although we’ve also seen how using the Tor Browser can bring unwanted attention.
Not to mention its Advanced Protection that blocks malicious sites, trackers, and ads. This is accompanied by the Network Lock kill switch that also prevents IP leaks. Some governments actively monitor or block Tor traffic, and Tor use can raise suspicion even when not used for illegal activities. Always verify a site’s legitimacy before visiting – onion addresses are long, random strings, making it easier for malicious actors to create lookalike addresses for phishing. A little typo can lead you to a clone designed to trick users into handing over sensitive data. While often used interchangeably, Tor and Tor Browser aren’t the same thing.
We review and list tools and products without bias, regardless of potential commissions. This is an estimated reading time to let you know how long it will take you to read all the content on this particular PrivacySavvy.com page. However, it has a sneak peek, easy guide steps, and/or a quick list providing quick in-page navigations and easily-found answers if desired. In contrast, VPN over Tor setups won’t protect your real IP address if Tor leaks, require more technical setup, and aren’t supported by many VPN providers. Research of the dark web is legal as long as national or international laws are not broken.



