
In an onion network, messages are encased in layers of encryption, much like the layers of an onion. The encrypted data is sent through a series of network-based nodes called onion routers. We don’t want to leave you with the impression that everything on the dark web is nefarious or illegal. The Tor network began as an anonymous communications channel, and it still serves a valuable purpose in helping people communicate in environments that are hostile to free speech. “A lot of people use it in countries where there’s eavesdropping or where internet access is criminalized,” Tiquet said.
- Treat Hidden Wiki with caution and verify any link via multiple sources.
- A logless VPN, which doesn’t store any traffic logs nor session logs is highly preferable.
- Beyond DuckDuckGo, other options have failed to keep up with the evolving landscape.
- We’ve compiled a detailed guide to help you explore the Top Darknet Markets.
- However, this does not provide any extra security for your device or information.
What Should I Avoid On The Dark Web?
To check, you can use dark web scanning or breach detection tools like Avast Hack Check or LifeLock Breach Detection to search for compromised data. If found, take immediate steps to secure your accounts and personal information. You can access the dark web on mobile with a dedicated dark web browser app. Install a mobile dark web browsing app — like Tor browser for Android or the Onion browser for iPhone — and enter an onion URL to start browsing. Only access the dark web with both a VPN and the Tor Browser active.

Facebook Onion Site
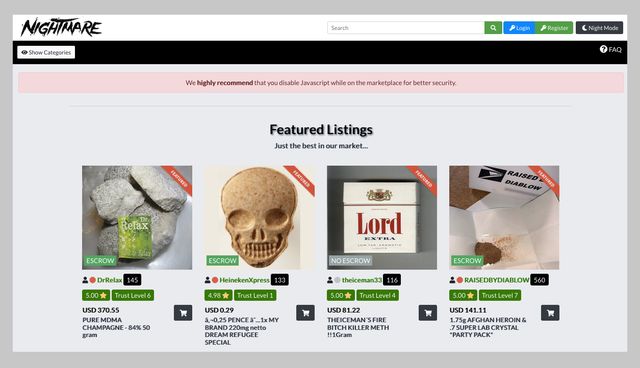
The dark web is infamous for containing sites such as Silk Road and other marketplaces where users could potentially buy drugs and/or weapons, stolen credit cards, IDs, and much more. The surface web (often referred to as the “visible web”) is the portion of the web available to the general public and indexed in the standard web search engines such as Google, Bing, and Yahoo. Sections of the dark web are often closed down too, as part of police operations.

What Is The Dark Web? How To Access It And What You’ll Find
The dashboard should open properly, indicating you’re ready to connect to any VPN server. This is just the first but also very important step to go to the dark web anonymously. Others were casual users—people buying fake IDs, stolen credit card numbers, or drugs.
Choosing a dark web monitoring tool requires a lot of factors, including price, availability, and many other things. However, effectiveness comes down to how well the tool aligns with your risk profile and operational needs. Lastly, keeping the Tor browser and any security software up to date is important for staying ahead of potential vulnerabilities. By following these tips, individuals can enhance their safety and privacy while exploring the Dark Web.
How To Install Red Hat Enterprise Linux (RHEL) 9 ? RHEL
VPN Over Tor is when you first connect to the Tor network and then connect to your VPN. While the Tor Browser does an excellent job of protecting your privacy and anonymity, you really shouldn’t use it as your daily driver browser. Open the Downloads folder on your Mac, and double-click the file you just downloaded.
What Should I Do If I Encounter Suspicious Links On The Dark Web?
The Deep Web forms a more expansive but hidden layer beyond the reach of conventional search engines. This section comprises content requiring specific permissions, login credentials, or specialized tools for access. Examples include password-protected websites, private databases, and subscription-based resources, contributing to a broader yet less visible realm on the internet. The dark web is the hidden section of the internet that can’t be found on regular, surface web search engines. To access the dark web, one would need to use a special anonymous browser called Tor. Tor provides users with a higher level of privacy, which is particularly attractive to threat actors, cybercriminals, hackers, and government operatives who want to keep their identities secret.
- Unlike Tor, I2P is designed for peer-to-peer services like file sharing, email, forums, and even decentralized websites — all within its own closed network.
- The Dark Web refers to hidden websites that aren’t indexed by regular search engines like Google or Bing.
- This multi-layered redirection ensures your actions leave no trace, offering a high level of anonymity.
- Typically, any reference to the visible web will be to common websites with a familiar internet domain extension.
- Understanding the differences and capabilities of various anonymity tools will help you make informed decisions about which networks best serve your needs.
Recommended Dark Web Search Engines And Directories
Well, VPN over Tor is basically its opposite – instead of going through the VPN first, the signal passes through the Tor network, before going through the VPN. Tor relays are servers run by volunteers, designed to keep your activities private and untraceable. Navigating the dark web requires extra layers of privacy, not just because of its content but due to legal scrutiny. The US Supreme Court has indicated that even casual browsing could lead to legal consequences. The Dark Web is a hidden part of the internet, completely different from the clear web we all use daily.
For instance, the Ashley Madison data dump was posted to a site only accessible to Tor users. By keeping an eye on these alternative platforms and trends, you gain a deeper understanding of how privacy, anonymity, and underground markets adapt to new technologies and challenges. As digital ecosystems morph, staying informed and agile will help you make the most of evolving privacy tools—or avoid stepping into ever-more complex traps. Avoid sharing personal information, downloading unknown files, and engaging in illegal services. Unlike Tor, I2P is designed for peer-to-peer services like file sharing, email, forums, and even decentralized websites — all within its own closed network.
Funnily enough, the deep web is the largest part of the internet! It’s online and you can access it but your friend or family can’t. One more thing before we move on – accessing the dark web is LEGAL.

Find Websites
The dark web has many legitimate use purposes and contains legitimate content, including dark web mirrors of popular websites and services such as BBC News and Facebook. Despite this, many people prefer not to advertise to their Internet Service Provider that they are accessing the dark web. The anonymity that the dark web provides attracts criminals, hackers, and malicious entities. Visiting dark web sites can expose users to malware, ransomware, and phishing attacks, putting personal and financial information at severe risk.
Some sites might offer tutorials or guides for aspiring cybercriminals. Some governments actively monitor dark web activity through various methods, like analyzing internet traffic patterns or using high-end surveillance software. Governments also often set up “honeypot” sites on the dark web, which mimic illegal services and wait for users to enter their info. Of course, this sort of site poses no risk to legitimate dark web users, but it’s worth knowing that your usage of the dark web in general might draw attention to you. A VPN adds that extra layer of privacy you need when browsing the dark web on Tor. Tor hides your IP address by routing your traffic through multiple encrypted layers, but that’s only in the Tor network.



