So, even though it does exist on the internet, Google doesn’t index any of these pages or content. We are reader supported and sometimes earn a commission if you buy through a link on our site. We deliver contextualized, actionable intelligence through our dedicated platform or API integration, ensuring that you can respond effectively to darknet threats. They use pseudonymous wallets, privacy coins (like Monero), mixers, chain-hopping, and non-KYC platforms to obscure transaction trails.
How Complex Are Dark Web Marketplaces Currently?
Understanding how this hidden corner of the Internet works matters more than ever. Journalists, security professionals and everyday users alike rely on its anonymity tools to safeguard whistleblowers, protect sensitive research and evade censorship. At the same time, criminals exploit the same architecture to traffic stolen data, malware and illicit goods.
It contains 7,500 terabytes of information, compared with only 19 terabytes of information in the “surface” web. To look at it in a different way, it makes up between 90% and 95% of the internet. Because of its anonymity, the dark web is filled with illegal services and is used by numerous criminal groups, including ransomware gangs. It is also used by whistle-blowers, journalists, and other individuals who are not involved in illegal activity but need to protect their communications and identities. Through the dark web, users in places of high censorship can also access information and news.
Is Tor Capable Of Accessing Surface Web Websites?

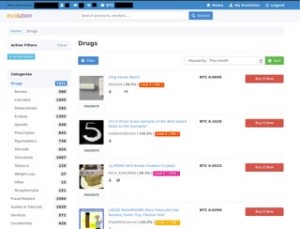
You can also run a dark web scan to see if your information has been leaked on the dark web. This dark web monitoring will help you track illicit activities and minimize the risks of cyber-attacks. Unlike other search engines, it does not collect or share web activities and personal data of users. Archetyp Market is a darknet marketplace that caters to a diverse range of transactions, operating exclusively within the Tor network.
The Tor Times
Finally, product variety significantly influences marketplace choice. Marketplaces that maintain strict moderation policies—banning excessively harmful or exploitative products—also gain popularity among more ethically minded users. Platforms that provide clear guidelines for maintaining operational security (OpSec) and offer built-in tools for data obfuscation are especially favored. To access the dark web, one needs to be sure they are maintaining all security and anonymity guidelines. A preferable choice always would be to buy a paid version of a VPN, but there are freely available VPN services as well.
Believe it or not, some dark web marketplaces have pretty advanced systems for building trust. Sellers often need to pay a deposit to prove they’re serious, and they build their reputation through positive reviews. As of 2020, nearly 57% of the dark web was estimated to contain illegal content, including violence and extremist platforms. The dark web marketplaces are mainly defined into two categories.
- The purpose was to protect U.S. army soldiers and agents in the field, but also politicians who held secret meetings and conversations, which contained the highest security measures.
- The deep web contains sites and pages that are often prevented from being indexed by search engines and contain unlinked content.
- Learn how darknet markets function and the challenges they present to cybersecurity, shedding light on the hidden side of the internet.
- In August 2021, co‑founder “DeSnake” relaunched AlphaBay with a decentralized infrastructure and stricter vendor vetting.
- This adds extra protection since opening Tor itself encrypts your traffic.
The marketplace has several rules that every user is bound to follow. If any user is found not complying with the law, strict and immediate action will be taken against them. It uses PGP encryption to protect sensitive data and messages, and accepts payments via Monera and Bitcoins to keep you anonymous on this marketplace. World Market is another largest dark web shops that deals with various goods and services. Its impressive anti-DDoS protection feature and easy-to-use interface make this marketplace stand out among the others.

How To Access The Dark Web?
In 2013, the FBI shut down the Silk Road, but it was later relaunched in 2014 with the new name of Silk Road 2.0, but the German authorities shut it down in the same year. Other than the Silk Road 2.0, similar marketplaces also emerged, but they all went down sooner or later. Besides this, it supports wallet-less transactions and accepts payments through Bitcoins, Litecoin, Monero, and Zcash. However, you must wait some time to reassess this marketplace because it’s been shut down. It issued a press release revealing that, from December 2021, the website won’t be functional anymore.
Security Blogs
In short, because of the nature of The Onion Routing, you can bypass all censorship and stay safe while doing so. In an era of rising digital surveillance and increasing cybercrime, the dark web represents both a warning and a tool. Use it to understand the boundaries of online freedom—and if you choose to explore it, do so with care, purpose and respect for the laws that govern your digital footprint. A reputable, no‑logs VPN hides Tor usage from your Internet service provider and prevents correlation attacks on the first hop.
What Is Tails Software Used For?
Tor stands for The Onion Router and it’s a browser based on Firefox, specifically made with accessing “.onion” websites in mind. The dark web has a bad reputation–and it comes by that reputation honestly. But that doesn’t mean it’s impossible to find and take down the bad guys. U.S. law enforcement and international partners have made several very high-profile seizures and arrests in recent months, proving that nobody stays anonymous forever. So, to recap, anything available to everyone via search is part of the open web, while any page behind credentials is part of the deep web and not available to search engines.
The real difference lies in what you can post and the poster’s anonymity. Unlike clear web forums, forums on the dark web are almost entirely anonymous and unregulated. Here, you can exchange ideas, ask questions, connect with like-minded people through social networking, or share documents and media via peer-to-peer (P2P) file sharing. Try LifeLock free for 30 days to receive notifications if we find your personal information on the dark web and help protect against identity theft. Farwa is an experienced InfoSec writer and cybersecurity journalist skilled in writing articles related to cybersecurity, AI, DevOps, Big Data, Cloud security, VPNs, IAM, and Cloud Computing.
It’s huge, making up about 90% of the internet, but it’s mostly mundane, hidden behind login screens for privacy and security. With all of that in mind, you need to tread carefully when browsing, in terms of the sites you visit and the other users you interact with. Bear in mind too that laws about freedom of speech and censorship vary from country to country, which is part of the reason the dark web exists in the first place.
In short, I’ll explain how Tor works and talk about its shortcomings. Tor bounces your traffic through multiple nodes or relays in the Tor network, which anonymizes your traffic as a result. The issue lies in its nodes, especially the entry node which is all but anonymous. Although, you’ll need special clearance to access it, such as the ability to log into your email account, pay for certain content, or be a part of a company network – you get the point. Instead, it uses the “.onion” domain which applies to all of its websites that also don’t have typical names. They’re instead a garbled mess of numbers and letters that are often changed to prevent tracking.

Darren Guccione is the CEO and co-founder of Keeper Security, the world’s most popular password manager and secure digital vault. Keeper is the first and only password management application to be preloaded with mobile operators and device manufacturers including, AT&T, Orange, America Movil and HTC. Keeper has millions of consumer customers and the business solution protects thousands of organizations worldwide. Law enforcement agencies keep an ear to the ground on the dark web looking for stolen data from recent security breaches that might lead to a trail to the perpetrators.
In fact, many of them spend their time on this part of the internet, so it’s vital to protect yourself with a VPN. You can use other “hidden Wiki” sites as well but I recommend this one because it offers dozens of dark web websites with frequently updated addresses. Needless to say, all you need to do is click on the site you want and it should open with no issues.



