
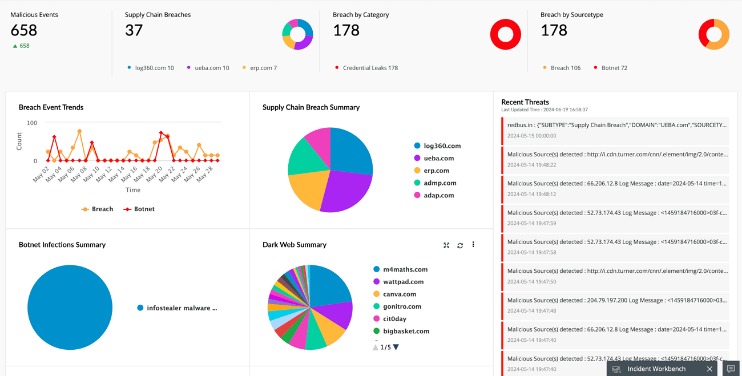
Collecting used keystrokes is how hackers typically guess credit card numbers, PINs, and passwords. A data breach occurs when confidential or protected information is exposed to unauthorized people or endpoints. Our platform can detect any suspicious mentions about organizations, or stolen payment information to give as much time as possible to prepare for data breaches. These systems can often identify when stolen card data is being tested before major fraud attempts begin. Banks and credit card companies lose billions annually to fraud, but the real cost isn’t just in fraudulent transactions. This type of malware silently infect payment terminals and exfiltrate card data in real-time.
Ready To Explore Web Data At Scale?
- He has consulted on digital fraud issues for dozens of top US, UK, EU, and Canadian banks and brokerages.
- Unlike many alternatives that allow user submissions without thorough vetting, we prioritize quality over quantity to maintain a safer browsing experience.
- With the growing threat from cybercriminals who sell stolen credit card information on the deep web and dark web, businesses need to stay ahead of the game.
- This makes it an essential resource for users living under oppressive regimes or in countries with strict internet controls.
- You can also share your virtual card details with family members without revealing your underlying bank information.
- Whistleblowers, journalists, and individuals living in repressive regimes often use the Dark Web to communicate securely and protect their privacy.
Back in the day, carding forums were the busiest of online crime hangouts, selling packs of stolen credit card data to anyone with the cash. That was then; now, you are more likely to find a roaring trade being made on the dark web in the likes of stolen passwords and account credentials, phishing exploit kits and malware-as-a-service platforms. A new report has revealed that the B1ack Stash crime forum has just given away more than a million stolen credit cards for free. The sooner you become aware of compromised information, such as stolen credit card numbers on dark web, the faster you can take steps to mitigate damage. Rapid response can prevent unauthorized transactions, minimize financial losses, and protect your customers’ trust in your business. However, it is the darker side of the Dark Web that captures the imagination of many.
Leveraging Outseer FraudAction Compromised Credit Card Feeds
- Of the Italian cards, roughly 50% have already been blocked due to the issuing banks having detected fraudulent activity, which means that the actually usable entries in the leaked collection may be as low as 10%.
- The origins of their fraud data between darknet, deep web, and surface web) was not specified in this impact report.
- Its philosophy centers on protecting user anonymity and avoiding the clutter that plagues other directories.
- We continuously monitor and update our directories to minimize risks and ensure users have access to trusted, legitimate sites.
- The impact of dark web credit card fraud extends far beyond individual card holders.
Avoid downloading the browser from unofficial sources to prevent malware or tampered versions. Once installed, the browser is simple to launch, and it automatically connects to the Tor network. This connection can take a few moments, depending on your internet speed and network conditions. Cryptocurrency tools help maintain privacy and trust during financial transactions on the dark web.
Where Is A Card Number On A Credit Card: A Simple Guide

Hundreds of millions of payment card details have been stolen from online retailers, banks and payments companies before being sold for cryptocurrency on online marketplaces such as UniCC. These stolen cards have value because they can be used to purchase high-value items or gift cards, which can then be resold for cash. This process is known as “carding”, and it has become a key part of the cybercriminal’s playbook. The technique is very profitable in its own right, but it is also used to help launder and cash-out cryptocurrency obtained through other types of cybercrime.
Useful Links
Abacus Market quickly rose to prominence by attracting former AlphaBay users and providing a comprehensive platform for a wide range of illicit activities. If you come across any instances of credit card fraud or encounter suspicious activities, it is essential to report them to relevant authorities. By doing so, you can contribute to mitigating the impact of these illegal activities and help protect innocent individuals from falling victim to financial fraud. It is essential to understand that participating in credit card transactions on the Dark Web is illegal and unethical. Engaging in illegal activities can lead to severe legal repercussions, including fines and imprisonment.
?️ Nonvbvshopcom – The Classic Underground Resurrected

This section is solely for informational purposes, and it is strongly advised to refrain from engaging in any illicit activities. Buyers must navigate through a labyrinth of fraudulent sellers and law enforcement operations targeting illegal marketplaces. It is crucial to exercise caution and take protective measures to safeguard personal information. These measures include implementing robust security practices, such as encryption and multi-factor authentication, to protect credit card data and reduce the likelihood of it ending up on the dark web. Carding forums — where cybercriminals chat about stealing card information, share tips for how to hack into websites and more — and marketplaces, where card data is actually bought and sold, are prolific on the dark web, Thomas says. Card Shops typically host the trade of credit cards and other stolen financial information, making it easy for cybercriminals to find what they’re looking for.
Assess Stablecoin Ecosystem Activity
The scale of this leak underscores the persistent vulnerabilities in global payment systems. By monitoring dark web markets, we often discover data breaches before they’re publicly reported. While consumers are typically protected from direct financial losses, dealing with credit card fraud is incredibly disruptive. As with credit cards, the location of the victim whose information is up for sale has a significant influence on price. Credit card details used for online fraud are cheaper and can be sent in a text message. Physical cards are usually cloned from details stolen online, but can be used to withdraw from ATMs.
Despite the pseudonymous nature of cryptocurrencies, law enforcement agencies and cybersecurity experts have developed sophisticated techniques to trace these transactions. Unlike the traditional web we use every day, with search engines indexing websites for easy discovery, the Dark Web operates on anonymous networks such as Tor. This anonymity allows criminals to conduct illegal activities without fear of being traced by law enforcement agencies. To minimize the risk of payment data exposure, only shop from reputable retailers, use digital payment methods or one-time private cards, and protect your accounts with two-factor authentication. Hundreds of millions of payment card details have been stolen from online retailers, banks and payment companies before being sold on online marketplaces such as UniCC.
Securing Virtualized Environments – Hypervisor Security Best Practices
If you suspect your card details have been stolen, you should immediately call your bank or credit card company. They can freeze the card and investigate further to trace usage details, suspicious activities, and other signs of theft. The stolen data reportedly includes a mix of credit and debit cards from major providers like Visa, MasterCard, American Express, and JCB.
Financial institutions can proactively strengthen their defences by integrating intelligence derived from FraudAction. This involves leveraging insights from compromised credit card feeds into security protocols, enabling institutions to identify potential threats, block fraudulent transactions, and enhance overall risk management. Indeed, in the last six months of 2020 alone, threat actors offered more than 45 million compromised cards for sale in underground credit-card markets monitored by security firm Cybersixgill, the company said in a report. These cards are then used by cybercriminals to make online purchases, including buying gift cards, that are hard to track back to them. Dark.fail has become one of the most trusted alternatives to the traditional Hidden Wiki. This directory focuses on providing users with verified, frequently updated links to a broad range of dark web services, including marketplaces, forums, and whistleblower platforms.
Card Verification Values (CVVs)
Sales of passports, driver’s licenses, frequent flyer miles, streaming accounts, dating profiles, social media accounts, bank accounts, and debit cards are also common, but not nearly as popular. In addition to PayPal account balances, they can also transfer money from any connected bank accounts or credit cards. On top of all that, they could make purchases or request money from contacts listed in the PayPal account.
Fullz that come with a driver’s license number, bank account statement, or utility bill will be worth more than those without, for example. Infosec Insider content is written by a trusted community of Threatpost cybersecurity subject matter experts. Each contribution has a goal of bringing a unique voice to important cybersecurity topics.
Remember, while evaluating seller feedback and ratings can provide valuable insights, engaging in credit card transactions on the Dark Web is illegal and carries significant risks. It is essential to proceed with caution and prioritize personal security and ethical considerations. The financial repercussions for victims can be debilitating, leading to damaged credit scores, fraudulent charges, and identity theft. Furthermore, participating in these illegal activities carries the constant risk of being caught by law enforcement agencies. UniCC has been active since 2013 with tens of thousands of new stolen credit cards listed for sale on the market each day. It is understood that the data included such highly sensitive information as the primary account number of the credit cards concerned, along with expiration dates and the card verification value, CVV2, security code.



