
It is known for strong encryption protocols and anti-DDoS protections, ensuring reliable access and user anonymity. Before Hidden Wiki is Daniel, a ‘dark web websites’ aggregator that can help you navigate the onion maze. Daniel acts as a dark web search engine to help users find reliable onion sites. Daniel regularly crawls the dark web searching for new websites or checking the status(es) of other websites.

A Dark Web Search Engine
In most cases, the deep web exists to protect privacy, enforce intellectual‑property rights or comply with regulations. Understanding these moving parts clarifies both the promise and peril of the dark web. The same relay system that shields whistleblowers also frustrates investigators; the same hidden addresses that protect dissidents can hide criminal storefronts. Mastering the postal‑route mechanics—and their limits—lets you weigh privacy gains against security risks before venturing into the hidden Internet. Based in Switzerland, Proton is protected by some of the world’s strongest privacy laws, which are designed to safeguard your data from unauthorized access, including from governments.
Best Onion Sites To Discover On The Dark Web In 2024
Whenever you’re on a dark web site, avoid dropping any personal information. Create anonymous profiles for any website you register with on the dark web. Additionally, ensure you do not visit websites or social media that might require you to drop your personal details. This VPN has various features that keep you safe on and off the dark web. It uses 256-bit AES encryption for maximum data protection, has a no-logs policy, and protects against IPv6, DNS, and WebRTC leaks. It prevents your IP address from ever falling into the wrong hands in the depths of the internet via “Network Lock,” its kill switch available across all major platforms.
Bonus: A Few More Dark Web Websites
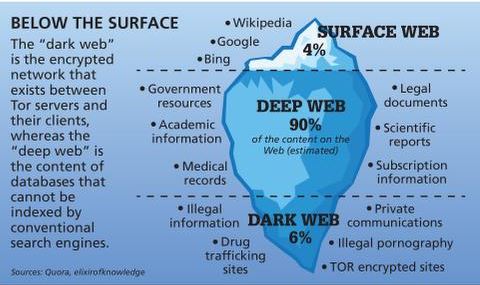
The surface web is the portion of the Internet that traditional search engines such as Google, Bing and DuckDuckGo can crawl and index. Pages here follow standard Web protocols, allow automated “spiders” to read their content and are designed for public consumption. When you type a query into a search bar and click a result—say, reading this very article or checking today’s weather forecast—you are on the surface web. Because its sites are openly linked, the surface web represents only a small fraction of total online content, but it feels vast because it is the most visible.
Every communication is encrypted, so even the simplest transaction requires a PGP key. These groups develop their own sophisticated malware, sometimes combined with pre-existing tools, and distribute them through “affiliates”. The dark web is a subset of the deep web that is intentionally hidden, requiring a specific browser—Tor—to access, as explained below. No one really knows the size of the dark web, but most estimates put it at around 5% of the total internet. Again, not all the dark web is used for illicit purposes despite its ominous-sounding name.
Avoid Sharing Personal Information
It acts as a centralized hub to access sites that are not indexed by traditional search engines like Google. Many users rely on the Hidden Wiki to find reliable dark web resources safely and efficiently. This includes password-protected sites, private databases, academic journals, and, notably, dark web services accessible only through networks like Tor or I2P. The Hidden Wiki is a gateway to these deep web resources, offering links to .onion sites that cannot be found via Google or other surface web search engines. Thus, users who want to explore hidden, uncensored, or private content often rely on tools like the Hidden Wiki because it provides structured access to resources beyond Google’s reach. Although it is true that the dark web can be a hotspot for illegal activities due to its anonymity, it’s not just for those with nefarious intentions.
Market admins use AI to detect scams, fake reviews and phishing links, while law enforcement deploys machine learning to map vendor reputations and analyze seizure data. In parallel, threat actors have begun using LLMs to auto‑generate malware listings and evade keyword filters, accelerating both growth and complexity. You’ll learn how it differs from the surface and deep webs, how Tor and similar networks maintain anonymity, and why some activities cross legal lines.
Malicious Software
Many dark web search engines on the darknet suffer from spam, because these spammy sites want to be indexed and found by the search engines as opposed to genuine onion sites. Vorm Web focuses on quality over quantity and splits findable results into three security categories, from secure to risky. The dark web might sound like a mysterious part of the internet, and in many ways, it is. It’s a segment of the internet hidden from view, not showing up in search results or accessible through regular web browsers. To enter this hidden world, users rely on the Tor browser, a specialized tool designed to keep web activity private by bouncing it through a network of relays around the globe.
Dark Web Sites
You can also use the Tails operating system to further protect yourself. If you’re just browsing the dark web out of curiosity, Tor, or a Tor and VPN configuration is safe enough. If you’re trying to hide from an oppressive government or want to be a whistle-blower for something illegal, take as many steps as you can to be safe. George is a seasoned Cybersecurity writer who has been writing guides and news about digital security for over five years.
It delivers an uncensored search experience, granting users access to a diverse array of information while effectively excluding illegal content. Dark web search engines are an alternative to having high technical knowledge, something hackers, journalists, and security firms are used to. With a single click of a button and going through some web pages, one can now easily visit a dark web page. It is that hidden corner of the internet that is hidden from the public and can only be used by a limited number of people.
If you want to learn all about privacy protection or cryptocurrency, the dark web has plenty to offer. There are a variety of private and encrypted email services, instructions for installing an anonymous operating system and advanced tips for the privacy-conscious. With all of that in mind, you need to tread carefully when browsing, in terms of the sites you visit and the other users you interact with.

- So, if the website looks fishy, close the tab, and forget about it.
- I possess a keen interest in exploring and understanding the intricacies of malware, Advanced Persistent Threats (APTs), and various cybersecurity challenges.
- Faktory’s website invites social connections with its interactive, modern design.
- If you can’t think of a strong password, consider using a password generator.
The dark web is part of the hidden web, which comprises non-indexed websites that are mostly used for illegal and illicit activity. If you have heard your peers or colleagues throw this term around and are wondering, “What is the dark web? Ahmia is a dark web search engine designed to index and search tor websites.
Here, you can exchange ideas, ask questions, connect with like-minded people through social networking, or share documents and media via peer-to-peer (P2P) file sharing. Dark web marketplaces are websites where you can exchange illicit goods and services like stolen credit cards, account login credentials, counterfeit items, drugs, and other items. Usually dark web transactions are made with Bitcoin or other cryptocurrencies. There are thousands of websites on the dark web, many—but not all—of which are illicit marketplaces selling stolen personal data.
However, on top of this basic file-hosting framework, volunteers have developed applications that allow for websites, message boards, and more. A limitation of this system is that websites cannot be dynamic (so they’re always simple static HTML pages). The dark web isn’t called “dark” because it’s inherently bad; it’s called dark because it provides privacy (that can be used for good and ill). The dark web is much like the regular World Wide Web we’re all familiar with, except that the dark web provides much greater privacy.
A cautious setup minimizes the chances of leaking your identity or infecting your device. Follow these four essential steps before you click a single .onion link. Such spaces let researchers and activists trade defensive know‑how without exposing their real‑world identities. Inside Tor, every hop is encrypted, but if you visit a non‑HTTPS surface‑web page, the segment from the exit relay to that site travels in clear text. Think of it as the courier handing your unsealed letter to the recipient’s mailbox. Using HTTPS (the lock icon) or a VPN‑over‑Tor adds another envelope.



