
Anyone can access the dark web, and it’s not that complicated to do so. This allows you to use the computer without the risk of corrupting your computer’s normal operating system with viruses or malware. Tails also protects you from possible malware, viruses, or keystroke loggers that may have already infected the computer, as it doesn’t run the operating system already installed on the device. The advantage of using a dedicated computer just to browse the dark web is that your main computer isn’t exposed to any of the threats or risks tied to entering the dark web.
Get News Alerts From PBS News

If you search the dark web, for instance, you’ll find online marketplaces that sell everything from Netflix passwords to stolen credit card account numbers. You’ll find other sites where you can buy illegal software, prepaid debit cards, and hackers for hire. Since the dark web operates in a largely unregulated environment, there is no way to ensure the legality or ethicality of the content being accessed.
‘Small Penis Rule’ Explained As South Park Creators Could Rely On It To Avoid Any Trump Legal Action
- This secret networkwould not be known or accessible to ordinary internet surfers.
- However, U.S. computer-enabled crimes are difficult to track, lowering the precision of global change estimates.
- The new regulations, which came into force last week, are meant to compel sites and apps to have “highly effective” age checkers to prevent users under 18 from accessing pornography.
- Abuse and persecution victims, whistleblowers, and political dissidents have been frequent users of these hidden sites.
- (The installation instructions that follow are for the macOS platform, I’ll mention where it’s different for Windows.) Simply double-click the downloaded file in your download folder.
For some users, portions of the deep web offer the opportunity to bypass local restrictions and access TV or movie services that may not be available in their local areas. Others go somewhat deeper to download pirated music or steal movies that aren’t yet in theaters. The deep web rests below the surface and accounts for approximately 90% of all websites. This would be the part of an iceberg beneath the water, much larger than the surface web.
Legal Uses Of The Dark Web

Verizon recently sold Tumblr to the web development company Automattic. Multiple police investigations over the past few years have broken up enormous dark web forums, including one known as Child’s Play that was reported to have had over a million user accounts. Increasingly, criminals are using advanced technologies like encryption to stay ahead of the police. In this case, the Ohio man, who helped run a website on the dark web known as the Love Zone, had over 3 million photos and videos on his computers. Congress has regularly allocated about half of the $60 million in yearly funding for state and local law enforcement efforts.
- The Justice Department says the arrests are connected to a 10-month investigation between federal law enforcement officials in the U.S. and Europol in Europe.
- All told,the site had generated sales totaling more than 9.5 million in Bitcoinvalued, at the time, at approximately $1.2 billion.
- Prosecutors said the site had offered videos of sex acts involving children, infants and toddlers – and specifically asked users not to upload videos featuring adults-only pornography.
- Knowledge, funding, and resources for probing the marketplace are insufficient to overcome the legal and technical challenges facing investigators.
- Many of these Reddits have rules prohibiting linking to illegal sites and services, so you likely won’t find anything illegal there.
Dark Web Myths Busted: What’s Legal And What’s Not?
In addition to contributing child pornography, he advised users on ways to avoid detection by law enforcement. Riseup is a volunteer-run collective that offers secure chat and email services primarily used by progressive activists and social justice communities. It’s maintained by an independent organization committed to digital privacy and security.
Stay One Step Ahead – Protect Your Data From The Dark Web

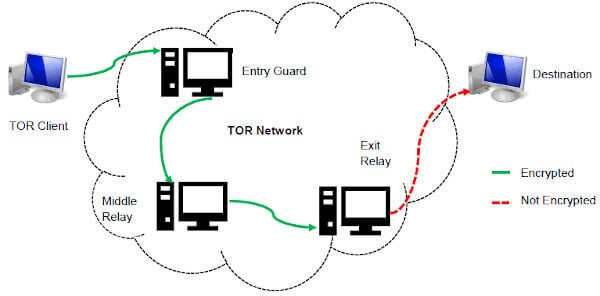
These sites are a hybrid tutorial-underground where wannabe hackers ask questions and professionals sell their services or stolen data. These are the primary sources of what the general public thinks of as “dark web.” Online marketplaces selling hacked credit cards, fake passports, malware kits, untraceable drugs, anything. With the onion browser, you can access ordinary HTTPS websites on the web. This is a great way to improve your privacy because Tor isolates each website you visit, meaning third-party trackers and ISPs can’t reveal your identity.
Attorneys for DeWitte and Tisoy did not respond to requests for comment. Humphrey said agents are in the process of “trying to use AI for good,” to sort through massive amounts of child sexual abuse material and speed up the process of trying to identify victims. In May, a Gloucester police officer was charged with receipt of child pornography after the FBI allegedly traced his IP address to a site on the dark web and found images on his phone and laptop, according to court filings. Dark web, websites not indexed by search engines and theoretically possible to visit with complete anonymity. You might consider investing in a VPN, or virtual private network, too, when accessing and searching the dark web. A VPN helps keeps you anonymous when searching the internet, whether you are scanning the surface web or the dark web.
Quick Links
But again, your ISP won’t be able to see any of the content you’re reading or what you are sending and receiving through the Tor network. It’s not a secret that ISPs (Internet Service Providers) and the FBI are tracking Tor users. Obviously not all Tor users, but you never know whether someone might be looking into you. It’s important to arm yourself with a good VPN (Virtual Private Network) when you want to enter the dark web to protect your privacy and anonymity.
To gain access to the group, prospective members allegedly had to upload a sexually explicit image of a naked child, younger than 13. A handwritten note with the chat group’s name had to appear in the photo or video to verify it was taken by the prospective member. Government cyber teams can take such websites down, arrest the owners and then use the website to track and follow users that show activity on the website. There’s a significant risk to dark web users of being exposed to malware (malicious software) infections. There are several programs that hackers frequently use on the dark web.

Identity theft monitoring is critical if you want to keep your private information from being misused. Passwords, physical addresses, bank account numbers, and social security numbers circulate in the dark web all the time. You may already be aware that malicious actors can use these to harm your credit, engage in financial theft, and breach of your other online accounts. Leaks of personal data can also lead to damage to your reputation via social fraud. Infiltrations can put you at risk of monitoring for other types of activity as well. Evading government restrictions to explore new political ideologies can be an imprisonable offense in some countries.

Even unintentionally viewing illegal content can result in criminal charges and severe penalties. Furthermore, the dark web is notorious for harboring malicious actors who may take advantage of unsuspecting visitors. Cybercriminals often use pornographic websites as a vector for malware, phishing scams, and identity theft. A spokeswoman for the center said it was common to expect corporations to provide financial assistance to charities. But the practice, others working in the area of child protection say, could elevate the interests of the tech companies above the children’s.
Are Sites On The Dark Web Illegal To Use And Visit?
In case of an attack, you can be sure that any of the data or information stored on your main computer will be safe. Unfortunately, it’s also a place where the bad guys can offer their services – for example, hackers or hitmen. These high levels of anonymity increase the opportunity for the “bad guys” to sell drugs, stolen IDs, credit cards, weapons, and many more compromised products or information.
Federal Bureau of Investigation agents executed a warrant to search Myran’s Bemidji apartment in December 2022, where they found several hard drives and a cellphone, according to court documents. Police have praised the work of their electronic crime investigations unit, which led to the arrests of Wilken and a number of other suspects. These sentiments come in the wake of the arrest of Darren Wilken, a Midrand man accused of creating and distributing child pornography on a global scale earlier this month.



