Yes, but you need to be cautious because there are many malicious sites on the dark web. The best way to do that is to get the link from legitimate sources, like The Hidden Wiki. What’s more, you should always use a VPN (like ExpressVPN) with Tor to protect yourself from IP leaks. I also recommend using an antivirus (like Norton 360) to protect your device from malware infections. ProPublica has a clearnet site, but its dark web version won’t see your IP address, so you get better privacy.
What Are Dark Web Websites?
However, data is required for understanding, monitoring, and improving the network. Furthermore, data will help to detect attacks against the network and possible censorship events. The BBC news website has a special .onion site, which you need to access via the dark web. Its goal is to offer anonymous access to the content without being censored, no matter where you live.
Dark Web Websites: 10 Onion Sites To Explore
It offers top-of-the-line security and fast speeds for a smooth browsing experience on the dark web. ActiveX and Java frameworks are susceptible to being exploited by hackers. Since you are navigating in uncharted territories with all the myriad threats today, you’ll have to disable them in your network settings to stay safe. Today, many organizations exist that are created only to handle these reports anonymously and effectively.
My favorites are DuckDuckGo (usually the Tor browser’s default search engine), The Hidden Wiki, and Ahmia. The Surface Web is the portion of the internet that we interact with on a daily basis. It’s made up of websites indexed by search engines, such as Google, Yahoo, or Bing. These are the websites we visit without thinking twice, like news outlets, e-commerce sites, blogs, and social media platforms. Archive Today, also known as Archive.is, is a web archiving service that captures, preserves, and provides access to snapshots of web pages. This capability makes it an invaluable tool for researchers, journalists, historians, and anyone interested in the preservation of digital content.
But online and at your finger tips, if you can make it past the surface web. Feather is a free and open source Monero wallet available on most major computer platforms. Monero is a crypto currency that can be used to conduct transactions anonymously on a peer to peer level without any centralized authority watching over.. The Dutch national police have made their onion site function as a billboard, warning all would-be criminals on darknet marketplaces to think twice about their actions. One of the most straightforward ways to access to dark web safely is via Tor, so we’ve kept that in mind when compiling our list.

Dark Web Search Engine
Otherwise, the first node in the onion relay system sees your real IP address, which can be used to locate you and unveil your identity. To help you make educated choices about cybersecurity to keep you (and your data) safe and secure, by providing detailed, accurate, and practical information based on thorough testing. Watch for unexpected changes in system performance that could indicate malware. Cryptocurrency miners and other malicious software often target dark web users. Using a reliable antivirus to scan your device is worthwhile if you spot suspicious spikes in system resource usage.
Vorm Web focuses on quality over quantity and splits findable results into three security categories, from secure to risky. In the deep net, web crawlers are blocked from accessing web pages to gather information for indexing, so the content remains hidden. Some content and services on the deep web are indexed by search engines, but paywalls or password protection prevent access. Content and services on the deep web are accessible through a regular browser. The dark web represents a much smaller segment of the deep web, accessible only through specialized tools like the Tor browser.
The Scale And Popularity Of DDoS-for-hire Services Is On The Up
A substantial portion of users turn to the Tor browser for its promise of anonymity, while others seek the additional security it provides. Curiosity about what the dark web has to offer also drives about one-third of its users. Surface web search engines can’t access the darknet, but specialized dark web search engines can help you find what you’re looking for. DuckDuckGo is a popular privacy-focused search engine that doesn’t track you across the web. DuckDuckGo’s dark web search engine may index pages on the dark web, but you’ll need to open it with Tor Browser.
The Best Onion Sites On The Dark Web In 2025
Once obtained, the articles are stored in its database, allowing users to search for and download research papers directly through the Sci-Hub website. DuckDuckGo also emphasizes transparent and customizable search experiences. Users have access to settings that allow them to control search parameters and privacy settings, further enhancing the personal security and customization of the search process. While the dark web has a reputation for hosting nefarious activities, it also serves legitimate purposes.
Roundup – Best VPNs For Speed
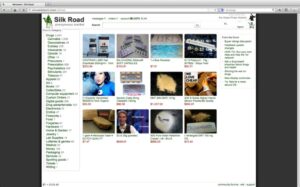
Many transactions conducted on the Dark Web involve the exchange of cryptocurrencies, as they offer a level of anonymity that traditional currencies cannot. For example, the Freedom of Information Foundation has long advocated for the use of the Dark Web in enabling free speech in repressive regimes. The most notorious marketplace to date was Silk Road, an online black market for drugs, which was shut down by the FBI in 2013. Despite this, similar markets have continued to emerge, fueling the Dark Web’s reputation as a haven for illegal trade. In this article, we’ll dive deep into the hidden world of the Dark Web, exploring its origins, structure, purposes, uses, risks, and the fascinating (and often dangerous) things that exist within it. One we’ve encountered is a scammer pretending to be the admin of an exclusive forum we tried to sign up for.
Common Scams On Dark Web Marketplaces
Proton Mail’s dark web version provides end-to-end encrypted email with enhanced privacy protection. The service doesn’t require personal information to create an account and works seamlessly through Tor. I found in my tests that all features work identically to the regular version. TorLinks maintains one of the most reliable directories of verified .onion sites. Its strength lies in regular updates and community-driven verification of links.
- With many Tor-based sites being overtaken by police authorities across the globe, there is a clear danger of becoming government target for simply visiting a dark website.
- So, when measuring the total network of live dark web sites alongside the surface web, only about 0.005% of the internet is the dark web.
- For additional protection, enterprises should monitor the dark web to identify indicators of dark web compromise, such as database dumps or the posting of personal or financial information.
- If the websites you visit use tracking scripts, third parties can monitor you.
- The Tor Browser is an open-source web browser created for anonymous browsing and to evade censorship.
- Once a user installs a dark web browser on a device, it functions like a regular browser.
Stolen credentials, trade secrets, and personal customer information are frequently sold on dark web marketplaces. Conducting regular cybersecurity assessments and implementing security gap analyses are essential measures to protect sensitive data. The dark web exists to address both legitimate and illegitimate needs in the digital landscape.
WANT TO TRY THE TOP VPN RISK FREE?
It is a good website for finding out which websites are currently working. If you need a listing of currently active websites, contact their support, and they will provide you with that. The Tor browser option for streaming comes with eleven channels with varying genres.
A top-of-the-line VPN network that ensures maximum security while accessing dark sites online. This includes military-grade 256-bit encryption reinforced with a 2048-bit DH key and SHA2-384 authentication to ensure your traffic arrives at its destination safely. This adds extra protection since opening Tor itself encrypts your traffic.