The dark web may offer access to valuable resources, but it’s also filled with traps, especially fake dark web sites designed to scam or harm unsuspecting users. One of the most common threats in 2025 comes from fraudulent marketplaces. These sites are crafted to look like real, trusted markets, complete with product listings, vendor ratings, and support pages. But once you send cryptocurrency to fund your account or make a purchase, the funds vanish — and so does the site. Many phishing sites imitate trusted platforms like the Hidden Wiki to trick users.
Scams And Phishing Attacks
I found it especially useful for testing new services without risking my main email address, though messages expire after 24 hours. DigDeeper offers in-depth analysis of technology and privacy topics rarely covered by mainstream media. The website’s articles focus on digital rights, surveillance, and security research. I found their technical explanations clear and well-researched, though the site updates less frequently than other news platforms. Although some of these markets prohibit certain extreme content such as violence or exploitation, most operate with very few rules beyond ensuring the security and anonymity of their users.
- Cracked.to, established in 2013, is a deep web forum that hosts discussions related to hacking, cracking, and data leaks.
- The dark web is always evolving, and that goes for the types of users it attracts.
- The Tor Network also allows users to access websites that are not indexed by major search engines.
- Ransomware attacks are expected to be carried out on supply chain operations of both smaller and high-value companies.
- Without the right precautions, your IP address could be exposed, leaving you vulnerable to hacking, tracking, or even identity theft.
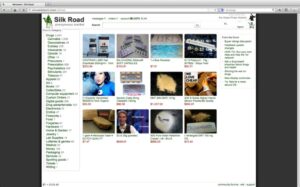
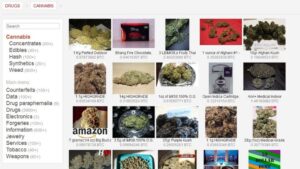
Nowadays, many people use the Tor browser to surf the public internet and navigate the deeper parts anonymously. Some markets even sell privacy tools, but you are more likely to run across counterfeit prescription pills and stolen identities. Some markets are relatively short-lived (thanks to law enforcement), but others are notorious enough that they survive, for instance, Silk Road, AlphaBay, and Hansa. With the onion browser, you can access ordinary HTTPS websites on the web. This is a great way to improve your privacy because Tor isolates each website you visit, meaning third-party trackers and ISPs can’t reveal your identity. Onion links have no regular domain names registered under the domain name registry.
Still, you might want to use additional security tools to protect your data when accessing these sites. Dark Websites can only be accessed using specialized privacy browsers, which encrypt your online data. Connect to the VPN before launching the Tor Browser, ensuring all your traffic is routed through the encrypted VPN tunnel first. Although this combination improves privacy, it can also further slow your connection speed, so balance your need for security with usability. Using a VPN is optional but highly recommended for users seeking maximum anonymity or those accessing sensitive content on the dark web.
Dark Web Marketplaces & Trends In 2025 Insights From SOCRadar & Cyble
- The dark web still hosts illegal marketplaces, scam sites, and dangerous content.
- Your data is encrypted in the Tor browser before reaching the ZeroBin servers.
- Cracked is one of the few dark web forums operating openly on the surface web.
- It also provides extra details about search results, such as page sizes.
- The Daniel site also had a status check feature that updated users on which sites were active.
Just as you explore hidden corners of the internet, you need to secure your data on the go. Easily initiate data encryption on your external drives and disks, ensuring compliance with your specific company policies. Encryption-2-Go offers controlled encryption, container-based or directory encryption, and even detects existing BitLocker To Go encrypted drives.
Abacus Market (Best For Cryptocurrency Transactions)
Versus Market allows users to leave detailed reviews, making it easier to identify trustworthy vendors. A quick guide for developers to automate mergers and acquisitions reports with Python and AI. Learn to fetch data, analyze content, and generate reports automatically. To get started on the dark web, the first step is to download a special browser. Each browser operates differently, so it is important to research each one to find out which one best fits your needs.
Some Of The Big Things On The Hidden Wiki You Should Know
Our curated list of legitimate dark web sites above offers a safe entry point for first-time explorers. It acts as a centralized hub to access sites that are not indexed by traditional search engines like Google. Many users rely on the Hidden Wiki to find reliable dark web resources safely and efficiently. Some dark web engines try to filter out illegal content or prioritize verified, non-malicious services. However, many present uncensored search results in their rawest form and expose users to a flood of stolen data, compromised credentials, and black market activity. While these platforms should never be used casually or without proper precautions, they offer unique visibility into potential threats that may otherwise go unnoticed.

Explore The Dark Web More Securely With A VPN
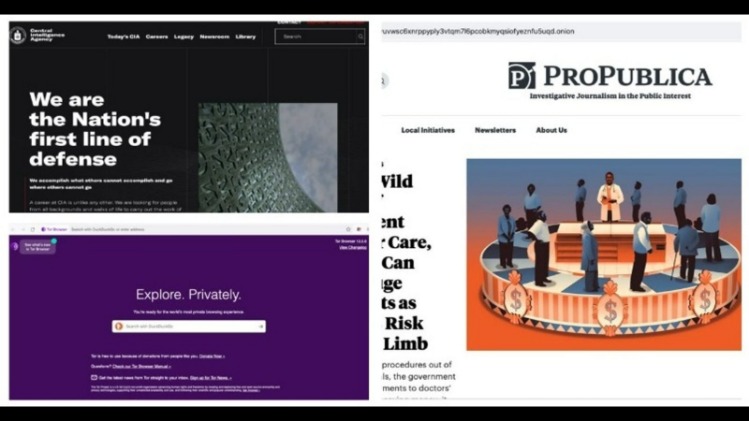
Offering a wealth of information about its operations, history, and initiatives, the CIA’s Tor platform provides insights into the workings of one of the world’s most enigmatic agencies. Designed to be used as a live system, it ensures that users leave no trace of their activities. The platform is regularly updated, ensuring that its index remains fresh and reflective of the ever-evolving Tor network. Galaxy2 offers a unique social networking experience on the Tor network. Offering a well-organized list of links spanning various categories, TorLinks serves as a reliable guide.

The Future Of Anonymity And Privacy Tools
No, Google and other search engines available on the regular part of the internet do not index .onion domains or any part of the Tor network. The dark web is intentionally hidden from surface web indexing, and to access it, you need a specialized dark web browser, like the Tor browser. Some dark web search engines include a manual vetting process to ensure relevance and safety.
Today’s cybercriminals spread their activities across multiple platforms, making them harder to track and shut down. It has a proprietary onion site in the Tor network to give you safe access even if your country restricts VPN usage. The most interesting thing about NordVPN is its built-in Onion over VPN feature. It encrypts your traffic at the entry node and changes your IP address.

And I liked that if I visited a site that had a .onion version, it prompted me to switch to that version. For example, the CIA has a dark web site for anonymous reporting services. Plus, dark web search engines can also allow political dissidents to bypass government censorship, or for journalists to safely engage with whistleblowers.
Here’s an overview of some of the most well-known dark web forums and deep web forums that have emerged over the years. Kaspersky report states, Last year, the underground market for cryptors—tools used by cybercriminals to obfuscate malicious code and evade detection—grew significantly. Developers introduced advanced techniques, advertising subscriptions ranging from $100 to $20,000.