His articles have appeared in many respected technology publications. Taking the necessary precautions makes tracing your activities on the dark web difficult. Although the Tor browser has sufficient encryption, combining it with a VPN offers better protection. However, you should not see it as an opportunity to engage in illegal activities to avoid trouble with authorities. This will help you to remain anonymous and secure at all Tor entry and exit nodes. It uses TrustedServer technology on the entire server network to wipe out your data after every session.
Is It Illegal To Visit And Use Dark Websites?

Instead, they are designed using a cryptographic key and can be accessed only through software like the Tor browser. ZeroBin is a wonderful way to share the content you get from dark web resources. It is a reliable messaging tool where you copy/paste a text or image and send it to your addressee. This is the best place to get short and reliable links to an unalterable record of any webpage across government and corporate websites. Unfortunately, it requires you to have an invitation code to create an account. This means you have to know someone who is already using the platform.
- Then get a VPN to help protect your privacy on dark web websites or wherever you browse online.
- Changing the Tor browser settings can further boost your security levels on the dark web shops.
- There’s nothing stopping sellers from packing up and leaving the market at any time.
- You should also consider freezing your credit to prevent identity theft.
In 2022, for example, BidenCash was linked to the breach of over 1.2 million credit card records. Using a VPN, such as Forest VPN, in conjunction with the Tor browser can significantly enhance your privacy. The VPN encrypts your connection and masks your IP address, providing an extra layer of security.
Note that loading sites with TOR usually takes considerably longer than on the clearnet. It may take anywhere from 15 seconds to several minutes for a page to load, depending on network and site demand. This highly popular English-language market sold all varieties of narcotics. Many of these markets operate internationally, and some have certain specialties.
Typical Use-Cases Of Dark-Web Marketplaces In 2025

The dark web, for the uninitiated among you, is a virtual neighborhood beyond the borders of the normal, everyday internet (which includes the website you’re looking at right now). It’s somewhere Google and Bing don’t index, and you need special tools to get to it. Any drug marketed as an opiate, be it pressed pills or heroin, may also contain amounts of tranquilizers or fentanyl. While pressed pills are often made with vitamins, it’s impossible to know that the additives are safe.
As of 2020, nearly 57% of the dark web was estimated to contain illegal content, including violence and extremist platforms. Darren Guccione is the CEO and co-founder of Keeper Security, the world’s most popular password manager and secure digital vault. Keeper is the first and only password management application to be preloaded with mobile operators and device manufacturers including, AT&T, Orange, America Movil and HTC.
News, Media, And Other Information Organizations
There are also many tools that can be use to monitor the dark web and scan for personally identifiable information and even respond to attacks. That’s why it’s important to verify links through trusted directories and proceed with caution. Fortunately, you can’t just stumble onto dark web websites by accident. Enable MFA wherever possible to protect your accounts from unauthorized access. Given the above threats, it’s a good idea to use Tor over a VPN to access the dark web. ZeroBin is an attractive option for anyone looking to share sensitive information without compromising privacy.
Hidden Answers
- The internet’s favorite alternative to Google made a name for itself by not logging your search activity yet still providing decent results.
- Renowned for its extensive inventory of financial data and sophisticated operating methods, Brian’s Club is a key player in the underground economy of financial cybercrime.
- The Camouflage Mode is intended for people living in countries with heavy internet censorship, like China.
- You can pay through Monera and Bitcoin using the escrow system or the traditional market account after making a purchase on this shop.
Bear in mind too, that your internet provider will be able to see you connecting to Tor nodes, even if it doesn’t know exactly what you’re doing. Many people install a VPN as well, but then you’re putting your trust in an additional third party to not track your activities or report them to anyone else. This market specialized in selling marijuana related products and magic mushrooms, with no “hard drugs” for sale. The Onion Project, or TOR is the predominant anonymous computer network.
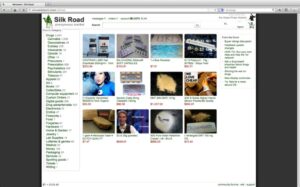
Darknet marketplaces may look like regular online stores, but using or even browsing them comes with serious risks. From identity theft to law enforcement surveillance, the dangers are real — and often underestimated. In recent years, leading dark web markets have grown more advanced. Some now offer customer support, escrow systems to prevent fraud, and even user-friendly interfaces that make illegal trade feel strangely routine. Still, the dangers are severe — exposure to scams, malware, surveillance, and prosecution are just the beginning. In this article, we’ll explore what dark web markets are, how they work, and why they’re so risky.
The Full List Of Trusted Darknet Markets:

Monitoring active marketplaces offers early access to malware kits, credential dumps, and fraud tools. Tracking vendor migration—such as from Archetyp to Exodus—provides insight into tactical shifts. Focusing intelligence collection on specialised marketplaces yields better ROI for threat detection and proactive defence. In 2025, darknet marketplaces primarily accept Monero (XMR) and Bitcoin (BTC). Privacy-focused operators are shifting to Monero due to its default anonymity, compared to Bitcoin’s transparent ledger Darknet markets see BTC inflow drop to $2B.
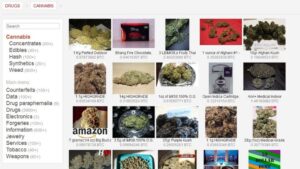
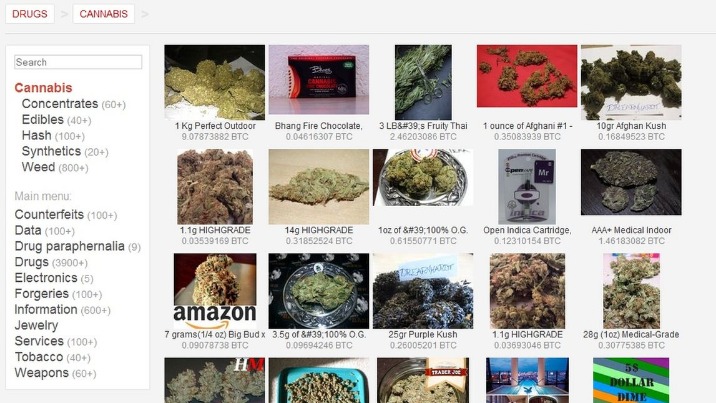
Topics And Products Sold
Use it to link your GitHub account, Twitter, Bitcoin address, and Facebook. This .onion link makes it impossible for hackers to impersonate your profile. Also, you can set a strong password to protect your message and choose how long it will take to expire.
The 9 Most Private Cryptocurrencies In 2025
Additionally, using antivirus software and strong passwords can further protect you from potential threats. Onion sites are websites on the dark web that use the ‘.onion’ top-level domain. They can only be accessed through the Tor browser, which encrypts your connection and masks your IP address, providing anonymity. While technically not an onion site, we’re including Sci-Hub (sci-hub.se) as an interesting example of a site you can access via Tor. Sci-Hub gives access to millions of scientific papers, mostly ones from behind paywalls. However, due to copyright infringement, Sci-Hub is considered illegal and banned in many countries.

For several years, Yahoo was at the apex as the internet’s best web service provider, offering… In today’s digital era, where information is constantly on the move across all digital platforms, an… It will route your traffic through multiple servers instead of one, making tracking your data and activities even harder.

A VPN hides the fact that you’re using Tor, which is blocked in some countries and always raises doubts because of its criminal reputation. If you want more peace of mind, NordVPN has a dark web monitoring tool you can consider using. This handy feature monitors the dark web for signs that your login details or other personal info have been leaked. However, the dark web is so complex and vast that if law enforcement takes down one market, it pops up elsewhere.
Why Are Darknet Markets Found On The Dark Web?
This is high-level protection; no one can intercept your data or activities. A budget-friendly VPN service allowing users to access dark web safely anytime, anywhere, and on any number of devices they want. A virtual private network (VPN) is a good way to mask Tor activities. It adds an extra encryption layer and passes your traffic through a secondary server of your choice, preventing anyone from seeing that you are accessing the web via Tor. Immediately close your entire Tor Browser window (not just that active tab).