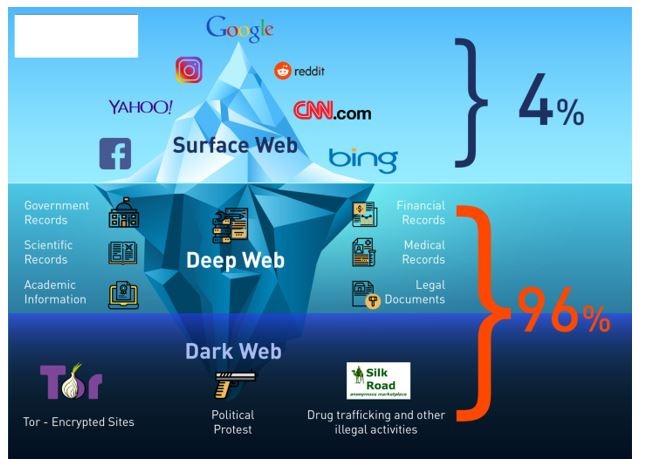
Think of it as an iceberg, with only a tiny part visible above the surface. If you dig deeper, you’ll discover the mysterious world of the deep web and, for the brave ones, the foreboding dark web. The dark web is a hidden part of the internet that can be accessed through limited resources. Moreover, you need to be more cautious while accessing it, as without proper safety, you can fall into the wrong hands and face serious consequences. Following are important tips you need to remember while visiting this dark part of the web.
Why Secure Access Matters
- However, if you must buy items from the dark web, set up a secure, encrypted email with CounterMail or ProtonMail.
- This means Tor is a lousy option for streaming video, online gaming, or downloading files (torrenting).
- In fact, they have a Telegram channel to offer users with live updates.
- In fact, a recent judgment by the US Supreme Court denoted that simply using Tor was sufficient probable cause for law enforcement to search and seize any computer around the world.
- Also, since the Tor Browser is based on the Mozilla Firefox platform, it’s susceptible to the same attacks that other browsers are.
- The Tor Browser is a modified version of the Mozilla Firefox browser and includes the TorButton, TorLauncher, NoScript, and HTTPS Everywhere Firefox extensions, along with the Tor proxy.
Most dark web marketplaces use cryptocurrencies like Bitcoin for transactions to help maintain anonymity. Once a buyer makes a payment, it’s usually held in escrow until they receive what they bought. For those venturing to the shadier side of the web or those who just want to know their identity is safe, dark web monitoring tools and identity theft protection are a must-have. Functionally, accessing DNMs and using them requires quite a few extra steps to protect the anonymity of the buyers, sellers, and server admins. To get into DNMs, you’ll likely have to figure out the basics of things like PGP encrypted messages and using the TOR browser. There are several ways to protect your online activities from being tracked.
Is Tor Browser Safe To Use?
Also, set up two-factor authentication (2FA) to add an extra layer of protection in case someone manages to figure out your password. Moreover, if you must use public Wi-Fi, ensure that you use a VPN to mask your browsing activity and keep yourself secure. The dark web is famous when it comes to hosting as well as spreading explicit and illegal content. It is home to all sorts of disturbing content, given that the markets share content related to non-consensual recordings and child exploitation. Interestingly, the hackers don’t hide, but most of them even openly advertise what they offer on the darknet forums. Therefore, you can hire them to perform a task for you, from planting malware to hacking email accounts and even breaking into various social media accounts.
User Reviews

Every potential participant’s credentials must be vigorously vetted before they can join. That way, they aim to create secure forums and limit outsiders like law enforcement. Likewise, law enforcement agencies each day continue to fine-tune their strategies to get past these networks. The darknet markets are a hotbed for selling stolen personal information. The stolen data can be just anything from full names, credit card details, passwords to social media accounts, bank account information, and social security details, among others. Nevertheless, most of the items in the darknet markets are illegal or heavily regulated.
Top 13 Dark Web Forums Of 2025 To Monitor

Chainanalysis, a blockchain analysis firm, conducted research that shows that the revenue decreased from $3.1 billion (2021) to $2 billion (2024). As mentioned earlier, launching a cyberattack doesn’t require any hacking skills. Even people with zero technical knowledge can buy phishing kits, ransomware, or stolen logins.
What Can I Do If My Personal Information Is On The Dark Web?

Here, you can exchange ideas, ask questions, connect with like-minded people through social networking, or share documents and media via peer-to-peer (P2P) file sharing. More often than not, law enforcement is targeting the sellers more than the buyers. Still, it isn’t unheard of for people to be arrested for buying drugs on DNMs. Once the website is coded, the policies created, the admins ready, and the hosting secured, the site goes live on the TOR network.

Risks And Dangers
Although these marketplaces are continuously shut down by law enforcement agencies, they still work today. Interestingly, new sites get more hype, and it even becomes difficult to shut them down, as they have better security than the older ones. It’s incredibly common for darknet marketplaces to be held for ransom by hackers or attackers. These attacks usually involve DDOSing (overloading) the service and demanding a crypto payment from the site admins to stop the attack. TOR Browser is a free, modified version of the Firefox web browser configured to connect to the TOR network. You may also use it to access the regular internet more anonymously.
📚 Contents
On the other hand, some people might visit Darknet Markets for lawful purposes such as research, journalistic work, or simply to explore online communities. It’s essential to know the local laws regarding online activities, and be cautious when using these platforms to avoid any potential issues. However, engaging in illegal activities, such as buying or selling drugs or weapons, is against the law. Always ensure that your online activities comply with the laws of your country. The dark web comes with its own set of tools and services, including web browsers and search engines (which I’ll get on to in a moment). Part of what makes the dark web the dark web is that you can’t access it through your normal web browser, nor can you look something up on it via a Google search.

Unlike darknet mode, opennet uses a handful of centralized servers in addition to the decentralized peer-to-peer network. Always exercise extreme caution when using publicly posted onion URLs. If you can’t get a personal recommendation from someone you trust, verify the URL from multiple sources. Obviously, finding these .onion websites is the first challenge, as they won’t show up in Google search results. You can’t just Google “Silk Road” and hope to land on the dark website.
And once you’re inside, one wrong click on a fake .onion site can expose your identity or infect your device with malware. The technology behind this anonymous connection is known as “onion routing,” which utilizes a layered approach to obscure data and protect users’ locations on the network. This means that the identities and locations of darknet users are hidden from public view and remain anonymous, even when interacting with other users or engaging in any online activity. There are many different ways to access the dark web, but navigating it can be tricky and dangerous if you don’t know what you’re doing. A VPN will give you an extra layer of protection and anonymity, making it much safer to explore the dark web. Yes, you definitely need a VPN if you want to access the dark web on your phone.
This was the initial framework for anonymous communication and file sharing. You can use dark web monitoring tools, such as NordVPN’s Dark Web Monitor, to check if your data has been leaked. These tools scan dark web forums and marketplaces for any signs of your compromised credentials.
(Presentation and polish isn’t quite so important on this part of the internet.) Click on any website link, and it’ll appear on screen, with its address at the top. DuckDuckGo is the default search engine inside the Tor browser, and once you turn on the Onionize toggle switch in the search box, you’re able to use it to find dark web links. These typically come with “.onion” after them, rather than something like “.com” as on the standard web. Open up Tor, and you won’t suddenly see the dark web staring back at you. Not only do you need a dark web browser, you need a dark web search engine too.
People visit this market to buy stolen credit cards, personal data, remote desktop account credentials, and logs gathered from information-stealing malware. It has a search option to let you find local and international products and services on the dark web. A lot of vendors from all over the world are registered here, offering an extensive range of products, including digital services, security tools, and other equipment.